Architecture Compliance
Introduction |
Terminology - The Meaning of Architecture Compliance |
Project Impact Assessments (Project Slices) |
Architecture Compliance Reviews |
Architecture Compliance Review Process |
Architecture Compliance Review Checklists |
Architecture Compliance Review Guidelines
This chapter provides guidelines for ensuring project compliance to the architecture.
Introduction
Ensuring the compliance of individual projects with the enterprise architecture is an essential aspect of architecture
governance (see Architecture Governance). To this end, the IT governance function within
an enterprise will normally define two complementary processes:
- The Architecture function will be required to prepare a series of Project Impact Assessments (see Project Impact Assessments (Project Slices)); i.e., project-specific views of the enterprise architecture that
illustrate how the enterprise architecture impacts on the major projects within the organization. (These are sometimes referred to
as project slices through the architecture.)
- The IT Governance function will define a formal Architecture Compliance review process (see Architecture Compliance Reviews) for reviewing the compliance of projects to the enterprise architecture.
Apart from defining formal processes, the architecture governance (see Architecture
Governance) function may also stipulate that the architecture function should extend beyond the role of architecture
definition and standards selection, and participate also in the technology selection process, and even in the commercial
relationships involved in external service provision and product purchases. This may help to minimize the opportunity for
misinterpretation of the enterprise architecture, and maximize the value of centralized commercial negotiation.
Terminology - The Meaning of Architecture Compliance
A key relationship between the architecture and the implementation lies in the definitions of the terms "conformant",
"compliant", etc. While terminology usage may differ between organizations, the concepts of levels of conformance illustrated in
Levels of Architecture Conformance should prove useful in formulating an IT compliance strategy.
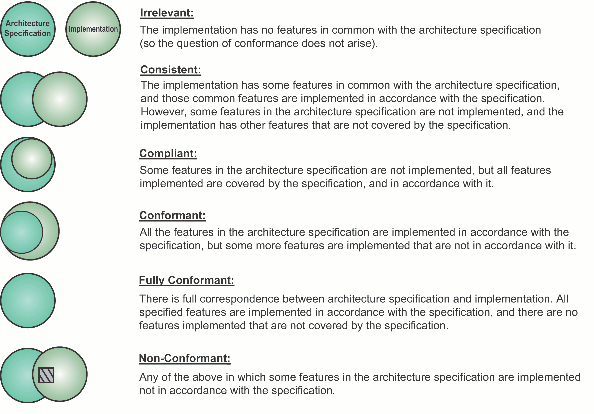
Figure: Levels of Architecture Conformance
The phrase "In accordance with" in Levels of Architecture Conformance means:
- Supports the stated strategy and future directions
- Adheres to the stated standards (including syntax and semantic rules specified)
- Provides the stated functionality
- Adheres to the stated principles; for example:
- Open wherever possible and appropriate
- Re-use of component building blocks wherever possible and appropriate
Project Impact Assessments (Project Slices)
Introduction
A "project slice" is a project-specific subset of the enterprise architecture. It is written in order to illustrate how the
enterprise architecture impacts on the major projects within the organization.
The structure of the description for each project is:
|
Introduction
|
Describes the project's business objectives, the applications being deployed, the major service qualities required
for the project, and the assumptions and constraints.
|
|
Target Architecture(s)
Mapping
|
Shows the business domain and Target Architecture coverage of the project, provides a system schematic, breaks down
the application into its logical partitioning and its physical topology, and (if relevant) provides a product table.
|
|
Project Development
Process Overview
|
Provides the project's key milestones, release schedule, and a roles, responsibilities, and contacts table.
|
|
Future Directions
|
Briefly outlines known future directions for the project.
|
|
References
|
Lists appropriate project documentation for further detail.
|
Sources
Much of this information will normally come from the projects themselves, and is not originated by the architect.
Project Impact Assessments will normally be developed as an output of Phase E of Part II: Architecture
Development Method (ADM).
It is important to note that, besides the ADM, an organization will often have other relevant methodologies - in particular, for
project management - that will have an input here.
There is also an important link to the architecture governance strategy (see Architecture
Governance). Defining a Project Impact Assessment is only worthwhile if project managers take notice of the impact!
Architecture Compliance Reviews
An Architecture Compliance review is a scrutiny of the compliance of a specific project against established architectural
criteria, spirit, and business objectives. A formal process for such reviews normally forms the core of an enterprise Architecture
Compliance strategy.
Purpose
The goals of an Architecture Compliance review include some or all of the following:
- First and foremost, catch errors in the project architecture early, and thereby reduce the cost and risk of changes required
later in the lifecycle. This in turn means that the overall project time is shortened, and that the business gets the bottom-line
benefit of the architecture development faster.
- Ensure the application of best practices to architecture work.
- Provide an overview of the compliance of an architecture to mandated enterprise standards.
- Identify where the standards themselves may require modification.
- Identify services that are currently application-specific but might be provided as part of the enterprise infrastructure.
- Document strategies for collaboration, resource sharing, and other synergies across multiple architecture teams.
- Take advantage of advances in technology.
- Communicate to management the status of technical readiness of the project.
- Identify key criteria for procurement activities (e.g., for inclusion in Commercial Off-The-Shelf (COTS) product RFI/RFP
documents).
- Identify and communicate significant architectural gaps to product and service providers.
Apart from the generic goals related to quality assurance outlined above, there are additional, more politically-oriented
motivations for conducting Architecture Compliance reviews, which may be relevant in particular cases:
- The Architecture Compliance review can be a good way of deciding between architectural alternatives, since the business
decision-makers typically involved in the review can guide decisions in terms of what is best for the business, as opposed to what
is technically more pleasing or elegant.
- The output of the Architecture Compliance review is one of the few measurable deliverables to the CIO to assist in
decision-making.
- Architecture reviews can serve as a way for the architecture organization to engage with development projects that might
otherwise proceed without involvement of the architecture function.
- Architecture reviews can demonstrate rapid and positive support to the enterprise business community:
- The enterprise architecture and Architecture Compliance helps ensure the alignment of IT projects with business
objectives.
- Architects can sometimes be regarded as being deep into technical infrastructure and far removed from the core business.
- Since an Architecture Compliance review tends to look primarily at the critical risk areas of a system, it often highlights the
main risks for system owners.
While compliance to architecture is required for development and implementation, non-compliance also provides a mechanism for
highlighting:
- Areas to be addressed for realignment
- Areas for consideration for integration into the architectures as they are uncovered by the compliance processes
The latter point identifies the ongoing change and adaptability of the architectures to requirements that may be driven by
indiscipline, but also allows for changes to be registered by faster moving changes in the operational environment. Typically
dispensations (see IT Governance) will be used to highlight these changes and set in
motion a process for registering, monitoring, and assessing the suitability of any changes required.
Timing
Timing of compliance activities should be considered with regard to the development of the architectures themselves.
Compliance reviews are held at appropriate project milestones or checkpoints in the project's lifecycle. Specific checkpoints
should be included as follows:
- Development of the architecture itself (ADM compliance)
- Implementation of the architecture(s) (architecture compliance)
Architecture project timings for assessments should include:
- Project initiation
- Initial design
- Major design changes
- Ad hoc
The Architecture Compliance review is typically targeted for a point in time when business requirements and the enterprise
architecture are reasonably firm, and the project architecture is taking shape, well before its completion.
The aim is to hold the review as soon as practical, at a stage when there is still time to correct any major errors or
shortcomings, with the obvious proviso that there needs to have been some significant development of the project architecture in
order for there to be something to review.
Inputs to the Architecture Compliance review may come from other parts of the standard project lifecycle, which may have an
impact on timing.
Governance and Personnel Scenarios
In terms of the governance and conduct of the Architecture Compliance review, and the personnel involved, there are various
possible scenarios:
- For smaller-scale projects, the review process could simply take the form of a series of questions that the project architect
or project leader poses to him or herself, using the checklists provided below, perhaps collating the answers into some form of
project report to management. The need to conduct such a process is normally included in overall enterprise-wide IT governance
policies.
- Where the project under review has not involved a practicing or full-time architect to date (for example, in an
application-level project), the purpose of the review is typically to bring to bear the architectural expertise of an enterprise
architecture function. In such a case, the enterprise architecture function would be organizing, leading, and conducting the
review, with the involvement of business domain experts. In such a scenario, the review is not a substitute for the involvement of
architects in a project, but it can be a supplement or a guide to their involvement. It is probable that a database will be
necessary to manage the volume of data that would be produced in the analysis of a large system or set of systems.
- In most cases, particularly in larger-scale projects, the architecture function will have been deeply involved in, and perhaps
leading, the development project under review. (This is the typical TOGAF scenario.) In such cases, the review will be co-ordinated
by the Lead Architect, who will assemble a team of business and technical domain experts for the review, and compile the answers to
the questions posed during the review into some form of report. The questions will typically be posed during the review by the
business and technical domain experts. Alternatively, the review might be led by a representative of an Architecture Board or some
similar body with enterprise-wide responsibilities.
In all cases, the Architecture Compliance review process needs the backing of senior management, and will typically be mandated
as part of corporate architecture governance policies (see Architecture Governance).
Normally, the enterprise CIO or enterprise Architecture Board (see Architecture Board)
will mandate architecture reviews for all major projects, with subsequent annual reviews.
Architecture Compliance Review Process
Overview
The Architecture Compliance review process is illustrated in Architecture Compliance Review Process
.
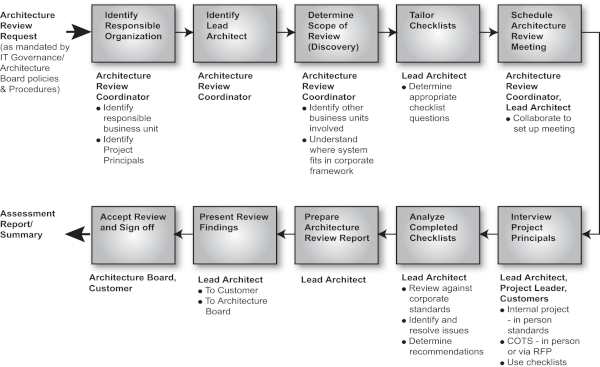
Figure: Architecture Compliance Review Process
Roles
The main roles in the process are tabulated below.
|
No.
|
Role
|
Responsibilities
|
Notes
|
|
1
|
Architecture Board
|
To ensure that IT architectures are consistent and support overall business needs.
|
Sponsor and monitor architecture activities.
|
|
2
|
Project Leader
(or Project Board)
|
Responsible for the whole project.
|
|
|
3
|
Architecture Review
Co-ordinator
|
To administer the whole architecture development and review process.
|
More likely to be business-oriented than technology-oriented.
|
|
4
|
Lead Architect
|
To ensure that the architecture is technically coherent and future-proof.
|
An IT architecture specialist.
|
|
5
|
Architect
|
One of the Lead Architect's technical assistants.
|
|
|
6
|
Customer
|
To ensure that business requirements are clearly expressed and understood.
|
Manages that part of the organization that will depend on the success of the IT described in the architecture.
|
|
7
|
Business Domain
Expert
|
To ensure that the processes to satisfy the business requirements are justified and understood.
|
Knows how the business domain operates; may also be the customer.
|
|
8
|
Project Principals
|
To ensure that the architects have a sufficiently detailed understanding of the customer department's processes.
They can provide input to the business domain expert or to the architects.
|
Members of the customer's organization who have input to the business requirements that the architecture is to
address.
|
Steps
The main steps in the process are tabulated below.
|
No.
|
Action
|
Notes
|
Who
|
|
1
|
Request architecture
review
|
As mandated by IT governance policies and procedures.
|
Anyone, whether IT or business-oriented, with an interest in or responsibility for the business area affected.
|
|
2
|
Identify responsible part of organization and relevant project principals.
|
|
Architecture Review Co-ordinator
|
|
3
|
Identify Lead Architect and other architects.
|
|
Architecture Review Co-ordinator
|
|
4
|
Determine scope of review
|
Identify which other business units/departments are involved.
Understand where the system fits in the corporate architecture framework.
|
Architecture Review Co-ordinator
|
|
5
|
Tailor checklists.
|
To address the business requirements.
|
Lead Architect
|
|
6
|
Schedule Architecture
Review Meeting
|
|
Architecture Review Co-ordinator with collaboration of Lead Architect.
|
|
7
|
Interview project principals
|
To get background and technical information:
- For internal project: in person
- For COTS: in person or via RFP
Use checklists.
|
Lead Architect and/or Architect, Project Leader, and Customers
|
|
8
|
Analyze completed checklists
|
Review against corporate standards.
Identify and resolve issues.
Determine recommendations.
|
Lead Architect
|
|
9
|
Prepare Architecture
Compliance review report
|
May involve supporting staff.
|
Lead Architect
|
|
10
|
Present review findings
|
To Customer
To Architecture Board
|
Lead Architect
|
|
11
|
Accept review and sign off
|
|
Architecture Board and Customer
|
|
12
|
Send assessment report/summary
to Architecture Review Co-ordinator
|
|
Lead Architect
|
Architecture Compliance Review Checklists
The following review checklists provide a wide range of typical questions that may be used in conducting Architecture Compliance
reviews, relating to various aspects of the architecture. The organization of the questions includes the basic disciplines of
system engineering, information management, security, and systems management. The checklists are based on material provided by a
member of The Open Group, and are specific to that organization. Other organizations could use the following checklists with other
questions tailored to their own particular needs.
The checklists provided contain too many questions for any single review: they are intended to be tailored selectively to the
project concerned (see Architecture Compliance Review Guidelines). The checklists actually used will
typically be developed/selected by subject matter experts. They are intended to be updated annually by interest groups in those
areas.
Some of the checklists include a brief description of the architectural principle that provokes the question, and a brief
description of what to look for in the answer. These extensions to the checklist are intended to allow the intelligent re-phrasing
of the questions, and to give the user of the checklist a feel for why the question is being asked.
Occasionally the questions will be written, as in RFPs, or in working with a senior project architect. More typically they are
expressed orally, as part of an interview or working session with the project.
The checklists provided here are designed for use in individual architecture projects, not for business domain architecture or
for architecture across multiple projects. (Doing an architecture review for a larger sphere of activity, across multiple business
processes and system projects, would involve a similar process, but the checklist categories and their contents would be
different.)
Hardware and Operating System Checklist
- What is the project's lifecycle approach?
- At what stage is the project in its lifecycle?
- What key issues have been identified or analyzed that the project believes will drive evaluations of hardware and operating
systems for networks, servers, and end-user devices?
- What system capabilities will involve high-volume and/or high-frequency data transfers?
- How does the system design impact or involve end-user devices?
- What is the quantity and distribution (regional and global) of usage, data storage, and processing?
- What applications are affinitized with your project by similarities in data, application services, etc.? To what degree is data
affinitized with your project?
- What hardware and operating system choices have been made before functional design of key elements of the system?
- If hardware and operating system decisions were made outside of the project's control:
- What awareness does the project have of the rationale for those decisions?
- How can the project influence those decisions as system design takes shape?
- If some non-standards have been chosen:
- What are the essential business and technical requirements for not using corporate standards?
- Is this supported by a business case?
- Have the assumptions in the business case been subject to scrutiny?
- What is your process for evaluating full lifecycle costs of hardware and operating systems?
- How has corporate financial management been engaged in evaluation of lifecycle costs?
- Have you performed a financial analysis of the supplier?
- Have you made commitments to any supplier?
- Do you believe your requirements can be met by only one supplier?
Software Services and Middleware Checklist
- Describe how error conditions are defined, raised, and propagated between application components.
- Describe the general pattern of how methods are defined and arranged in various application modules.
- Describe the general pattern for how method parameters are defined and organized in various application modules. Are [in],
[in/out], [out] parameters always specified in the same order? Do Boolean values returned by modules have a consist outcome?
- Describe the approach that is used to minimize the number of round-trips between client and server calls, particularly for
out-of-process calls, and when complex data structures are involved.
- Describe the major data structures that are passed between major system components.
- Describe the major communication protocols that are used between major system components.
- Describe the marshaling techniques that are used between various system components. Describe any specialized marshaling
arrangements that are used.
- Describe to what extent the system is designed with stateful and stateless components.
- Describe how and when state is saved for both stateful and stateless components.
- Describe the extent to which objects are created, used, and destroyed versus re-used through object pooling.
- Describe the extent to which the system relies on threading or critical section coding.
- Describe the approach and the internal documentation that is used internally in the system to document the methods, methods
arguments, and method functionality.
- Describe the code review process that was used to build the system.
- Describe the unit testing that has been used to test the system components.
- Describe the pre and post-condition testing that is included in various system modules.
- Describe the assertion testing that is included with the system.
- Do components support all the interface types they need to support or are certain assumptions made about what types of
components will call other components either in terms of language bindings or other forms of marshaling?
- Describe the extent to which big endian or little endian data format problems need to be handled across different
platforms.
- Describe if numbers or strings need to be handled differently across different platforms.
- Describe whether the software needs to check for floating-point round-off errors.
- Describe how time and data functions are Year 2000-compliant.
- Describe what tools or processes have been used to test the system for memory leaks, reachability, or general robustness.
- Describe the layering of the systems services software. Describe the general number of links between major system components.
Is the system composed of a lot of point-to-point interfaces or are major messaging backbones used instead?
- Describe to what extent the system components are either loosely coupled or tightly coupled.
- What requirements does the system need from the infrastructure in terms of shared libraries, support for communication
protocols, load balancing, transaction processing, system monitoring, naming services, or other infrastructure services?
- Describe how the system and system components are designed for refactoring.
- Describe how the system or system components rely on common messaging infrastructure versus a unique point-to-point
communication structure.
Applications Checklists
Infrastructure (Enterprise Productivity) Applications
- Is there need for capabilities that are not provided through the enterprise's standard infrastructure application products? For
example:
- Collaboration
- Application sharing
- Video conferencing
- Calendaring
- Email
- Workflow management
- Publishing/word processing applications
- HTML
- SGML and XML
- Portable document format
- Document processing (proprietary format)
- Desktop publishing
- Spreadsheet applications
- Presentation applications
- Business presentations
- Image
- Animation
- Video
- Sound
- CBT
- Web browsers
- Data management applications
- Database interface
- Document management
- Product data management
- Data warehouses/mart
- Program management applications
- Project management
- Program visibility
- Describe the business requirements for enterprise infrastructure application capabilities that are not met by the standard
products.
Business Applications
- Are any of the capabilities required provided by standard products supporting one or more line-of-business applications? For
example:
- Business Acquisition applications
- Engineering applications
- Computer-aided design
- Computer aided engineering
- Mathematical and statistics analysis
- Supplier management applications
- Supply chain management
- Customer relationship management
- Manufacturing applications
- Enterprise Resource Planning (ERP) applications
- Manufacturing execution systems
- Manufacturing quality
- Manufacturing process engineering
- Machine and adaptive control
- Customer support applications
- Airline logistics support
- Maintenance engineering
- Finance applications
- People applications
- Facilities applications
- Information systems applications
- Systems engineering
- Software engineering
- Web developer tools
- Integrated development environments
- Lifecycle categories
- Functional categories
- Specialty categories
- Computer-aided manufacturing
- e-Business enablement
- Business process engineering
- Statistical quality control
- Describe the process requirements for business application capabilities that are not met by the standard products.
Application Integration Approach
- What integration points (business process/activity, application, data, computing environment) are targeted by this
architecture?
- What application integration techniques will be applied (common business objects [ORBs], standard data definitions [STEP, XML,
etc], common user interface presentation/desktop)?
Information Management Checklists
Data Values
- What are the processes that standardize the management and use of the data?
- What business process supports the entry and validation of the data? Use of the data?
- What business actions correspond to the creation and modification of the data?
- What business actions correspond to the deletion of the data and is it considered part of a business record?
- What are the data quality requirements required by the business user?
- What processes are in place to support data referential integrity and/or normalization?
Data Definition
- What are the data model, data definitions, structure, and hosting options of purchased applications (COTS)?
- What are the rules for defining and maintaining the data requirements and designs for all components of the information
system?
- What shareable repository is used to capture the model content and the supporting information for data?
- What is the physical data model definition (derived from logical data models) used to design the database?
- What software development and data management tools have been selected?
- What data owners have been identified to be responsible for common data definitions, eliminating unplanned redundancy,
providing consistently reliable, timely, and accurate information, and protecting data from misuse and destruction?
Security/Protection
- What are the data entity and attribute access rules which protect the data from unintentional and unauthorized alterations,
disclosure, and distribution?
- What are the data protection mechanisms to protect data from unauthorized external access?
- What are the data protection mechanisms to control access to data from external sources that temporarily have internal
residence within the enterprise?
Hosting, Data Types, and Sharing
- What is the discipline for managing sole-authority data as one logical source with defined updating rules for physical data
residing on different platforms?
- What is the discipline for managing replicated data, which is derived from operational sole-authority data?
- What tier data server has been identified for the storage of high or medium-critical operational data?
- What tier data server has been identified for the storage of type C operational data?
- What tier data server has been identified for the storage of decision support data contained in a data warehouse?
- What Database Management Systems (DBMSs) have been implemented?
Common Services
- What are the standardized distributed data management services (e.g., validation, consistency checks, data edits, encryption,
and transaction management) and where do they reside?
Access Method
- What are the data access requirements for standard file, message, and data management?
- What are the access requirements for decision support data?
- What are the data storage and the application logic locations?
- What query language is being used?
Security Checklist
- Security Awareness: Have you ensured that the corporate security policies and guidelines to which you are designing are
the latest versions? Have you read them? Are you aware of all relevant computing security compliance and risk acceptance processes?
(Interviewer should list all relevant policies and guidelines.)
- Identification/Authentication: Diagram the process flow of how a user is identified to the application and how the
application authenticates that the user is who they claim to be. Provide supporting documentation to the diagram explaining the
flow from the user interface to the application/database server(s) and back to the user. Are you compliant with corporate policies
on accounts, passwords, etc?
- Authorization: Provide a process flow from beginning to end showing how a user requests access to the application,
indicating the associated security controls and separation of duties. This should include how the request is approved by the
appropriate data owner, how the user is placed into the appropriate access-level classification profile, how the user ID, password,
and access is created and provided to the user. Also include how the user is informed of their responsibilities associated with
using the application, given a copy of the access agreement, how to change password, who to call for help, etc.
- Access Controls: Document how the user IDs, passwords, and access profiles are added, changed, removed, and documented.
The documentation should include who is responsible for these processes.
- Sensitive Information Protection: Provide documentation that identifies sensitive data requiring additional protection.
Identify the data owners responsible for this data and the process to be used to protect storage, transmission, printing, and
distribution of this data. Include how the password file/field is protected. How will users be prevented from viewing someone
else's sensitive information? Are there agreements with outside parties (partners, suppliers, contractors, etc.) concerning the
safeguarding of information? If so, what are the obligations?
- Audit Trails and Audit Logs: Identify and document group accounts required by the users or application support,
including operating system group accounts. Identify and document individual accounts and/or roles that have superuser type
privileges, what these privileges are, who has access to these accounts, how access to these accounts are controlled, tracked, and
logged, and how password change and distribution are handled, including operating system accounts. Also identify audit logs, who
can read the audit logs, who can modify the audit logs, who can delete the audit logs, and how the audit logs are protected and
stored. Is the user ID obscured in the audit trails?
- External Access Considerations: Will the application be used internally only? If not, are you compliant with corporate
external access requirements?
System Management Checklist
- What is the frequency of software changes that must be distributed?
- What tools are used for software distribution?
- Are multiple software and/or data versions allowed in production?
- What is the user data backup frequency and expected restore time?
- How are user accounts created and managed?
- What is the system license management strategy?
- What general system administration tools are required?
- What specific application administration tools are required?
- What specific service administration tools are required?
- How are service calls received and dispatched?
- Describe how the system is uninstalled.
- Describe the process or tools available for checking that the system is properly installed.
- Describe tools or instrumentation that are available that monitor the health and performance of the system.
- Describe the tools or process in place that can be used to determine where the system has been installed.
- Describe what form of audit logs are in place to capture system history, particularly after a mishap.
- Describe the capabilities of the system to dispatch its own error messages to service personnel.
System Engineering/Overall Architecture Checklists
General
- What other applications and/or systems require integration with yours?
- Describe the integration level and strategy with each.
- How geographically distributed is the user base?
- What is the strategic importance of this system to other user communities inside or outside the enterprise?
- What computing resources are needed to provide system service to users inside the enterprise? Outside the enterprise and using
enterprise computing assets? Outside the enterprise and using their own assets?
- How can users outside the native delivery environment access your applications and data?
- What is the life expectancy of this application?
- Describe the design that accommodates changes in the user base, stored data, and delivery system technology.
- What is the size of the user base and their expected performance level?
- What performance and stress test techniques do you use?
- What is the overall organization of the software and data components?
- What is the overall service and system configuration?
- How are software and data configured and mapped to the service and system configuration?
- What proprietary technology (hardware and software) is needed for this system?
- Describe how each and every version of the software can be reproduced and re-deployed over time.
- Describe the current user base and how that base is expected to change over the next three to five years.
- Describe the current geographic distribution of the user base and how that base is expected to change over the next three to
five years.
- Describe the how many current or future users need to use the application in a mobile capacity or who need to work
off-line.
- Describe what the application generally does, the major components of the application, and the major data flows.
- Describe the instrumentation included in the application that allows for the health and performance of the application to be
monitored.
- Describe the business justification for the system.
- Describe the rationale for picking the system development language over other options in terms of initial development cost
versus long-term maintenance cost.
- Describe the systems analysis process that was used to come up with the system architecture and product selection phase of the
system architecture.
- Who besides the original customer might have a use for or benefit from using this system?
- What percentage of the users use the system in browse mode versus update mode?
- What is the typical length of requests that are transactional?
- Do you need guaranteed data delivery or update, or does the system tolerate failure?
- What are the up-time requirements of the system?
- Describe where the system architecture adheres or does not adhere to standards.
- Describe the project planning and analysis approach used on the project.
Processors/Servers/Clients
- Describe the client/server Applications Architecture.
- Annotate the pictorial to illustrate where application functionality is executed.
Client
- Are functions other than presentation performed on the user device?
- Describe the data and process help facility being provided.
- Describe the screen-to-screen navigation technique.
- Describe how the user navigates between this and other applications.
- How is this and other applications launched from the user device?
- Are there any inter-application data and process sharing capabilities? If so, describe what is being shared and by what
technique/technology.
- Describe data volumes being transferred to the client.
- What are the additional requirements for local data storage to support the application?
- What are the additional requirements for local software storage/memory to support the application?
- Are there any known hardware/software conflicts or capacity limitations caused by other application requirements or situations
which would affect the application users?
- Describe how the look-and-feel of your presentation layer compares to the look-and-feel of the other existing
applications.
- Describe to what extent the client needs to support asynchronous and/or synchronous communication.
- Describe how the presentation layer of the system is separated from other computational or data transfer layers of the
system.
Application Server
- Can/do the presentation layer and application layers run on separate processors?
- Can/do the application layer and data access layer run on separate processors?
- Can this application be placed on an application server independent of all other applications? If not, explain the
dependencies.
- Can additional parallel application servers be easily added? If so, what is the load balancing mechanism?
- Has the resource demand generated by the application been measured and what is the value? If so, has the capacity of the
planned server been confirmed at the application and aggregate levels?
Data Server
- Are there other applications, which must share the data server? If so, please identify them and describe the data and data
access requirements.
- Has the resource demand generated by the application been measured and what is the value? If so, has the capacity of the
planned server been confirmed at the application and aggregate levels?
COTS (where applicable)
- Is the vendor substantial and stable?
- Will the enterprise receive source code upon demise of the vendor?
- Is this software configured for the enterprise's usage?
- Is there any peculiar A&D data or processes that would impede the use of this software?
- Is this software currently available?
- Has it been used/demonstrated for volume/availability/service-level requirements similar to those of the enterprise?
- Describe the past financial and market share history of the vendor.
System Engineering/Methods & Tools Checklist
- Do metrics exist for the current way of doing business?
- Has the system owner created evaluation criteria that will be used to guide the project? Describe how the evaluation criteria
will be used.
- Has research of existing architectures been done to leverage existing work? Describe the method used to discover and
understand. Will the architectures be integrated? If so, explain the method that will be used.
- Describe the methods that will be used on the project:
- For defining business strategies
- For defining areas in need of improvement
- For defining baseline and target business processes
- For defining transition processes
- For managing the project
- For team communication
- For knowledge management, change management, and configuration management
- For software development
- For referencing standards and statements of direction
- For quality assurance of deliverables
- For design reviews and deliverable acceptance
- For capturing metrics
- Are the methods documented and distributed to each team member?
- To what extent are team members familiar with these methods?
- What processes are in place to ensure compliance with the methods?
- Describe the infrastructure that is in place to support the use of the methods through the end of the project and anticipated
releases.
- How is consultation and trouble-shooting provided?
- How is training coordinated?
- How are changes and enhancements incorporated and cascaded?
- How are lessons learned captured and communicated?
- What tools are being used on the project? (Please specify versions and platforms). To what extent are team members familiar
with these tools?
- Describe the infrastructure that is in place to support the use of the tools through the end of the project and anticipated
releases?
- How is consultation and trouble-shooting provided?
- How is training coordinated?
- How are changes and enhancements incorporated and cascaded?
- How are lessons learned captured and communicated?
- Describe how the project will promote the re-use of its deliverables and deliverable content.
- Will the architecture designs "live" after the project has been implemented? Describe the method that will be used to
incorporate changes back into the architecture designs.
- Were the current processes defined?
- Were issues documented, rated, and associated to current processes? If not, how do you know you are fixing something that is
broken?
- Were existing/planned process improvement activities identified and associated to current processes? If not, how do you know
this activity is not in conflict with or redundant to other Statements of Work?
- Do you have current metrics? Do you have forecasted metrics? If not, how do you know you are improving something?
- What processes will you put in place to gather, evaluate, and report metrics?
- What impacts will the new design have on existing business processes, organizations, and information systems? Have they been
documented and shared with the owners?
Architecture Compliance Review Guidelines
Guidelines for Tailoring the Checklists
- Focus on:
- High risk areas
- Expected (and emergent) differentiators
- For each question in the checklist, understand:
- The question itself
- The principle behind it
- What to look for in the responses
- Ask subject experts for their views
- Fix the checklists questions for your use
- Bear in mind the need for feedback to the Architecture Board
Guidelines for Conducting Architecture Compliance Reviews
- Understand clearly the objectives of those soliciting the review; and stay on track and deliver what was asked for. For
example, they typically want to know what is right or wrong with the system being architected; not what is right or wrong with the
development methodology used, their own management structure, etc. It is easy to get off-track and discuss subjects that are
interesting and perhaps worthwhile, but not what was solicited. If you can shed light and insight on technical approaches, but the
discussion is not necessary for the review, volunteer to provide it after the review.
- If it becomes obvious during the discussion that there are other issues that need to be addressed, which are outside the scope
of the requested review, bring it up with the meeting chair afterwards. A plan for addressing the issues can then be developed in
accordance with their degree of seriousness.
- Stay "scientific". Rather than: "We like to see large databases hosted on ABC rather than XYZ.", say things
like: "The downtime associated with XYZ database environments is much greater than on ABC database environments.
Therefore we don't recommend hosting type M and N systems in an XYZ environment."
- Ask "open" questions; i.e., questions that do not presume a particular answer.
- There are often "hidden agendas" or controversial issues among those soliciting a review, which you probably won't know
up-front. A depersonalized approach to the discussions may help bridge the gaps of opinion rather than exacerbate them.
- Treat those being interviewed with respect. They may not have built the system "the way it should be", but they probably did
the best they could under the circumstances they were placed in.
- Help the exercise become a learning experience for you and the presenters.
- Reviews should include detailed assessment activities against the architectures and should ensure that the results are stored
in the Enterprise Continuum.
return to top of page
Navigation
The TOGAF document set is designed for use with frames. To navigate around the document:
- In the main Contents frame at the top of the page, click the relevant hyperlink (Part I, Part II, etc.) to load the Contents
List for that Part of the TOGAF document into the Secondary Index frame in the left margin.
- Then click in that Contents List to load a page into this main frame.
return to top of page
Downloads
Downloads of the TOGAF documentation, are available under license from the TOGAF information web site. The license is free to any
organization wishing to use TOGAF entirely for internal purposes (for example, to develop an information system architecture for
use within that organization). A hardcopy book is also available from The Open Group Bookstore as document G063.
Copyright © 1999-2006 The Open Group, All Rights Reserved
TOGAF is a trademark of The Open Group


