Previous section.
Common Security: CDSA and CSSM, Version 2 (with corrigenda)
Copyright © 2000 The Open Group
Signed Manifests-The Architecture
Signed manifests describe the integrity and authenticity of a
collection of digital objects, where the collection is specified as an
acyclic connected graph with an arbitrary number of nodes representing
arbitrary typed digital objects. Digital signaturing based on public
key infrastructure is the basic integrity mechanism for manifests. The
signed manifest is data type-agnostic allowing referents in the
manifest to be other signed manifests or other types of signed
objects.
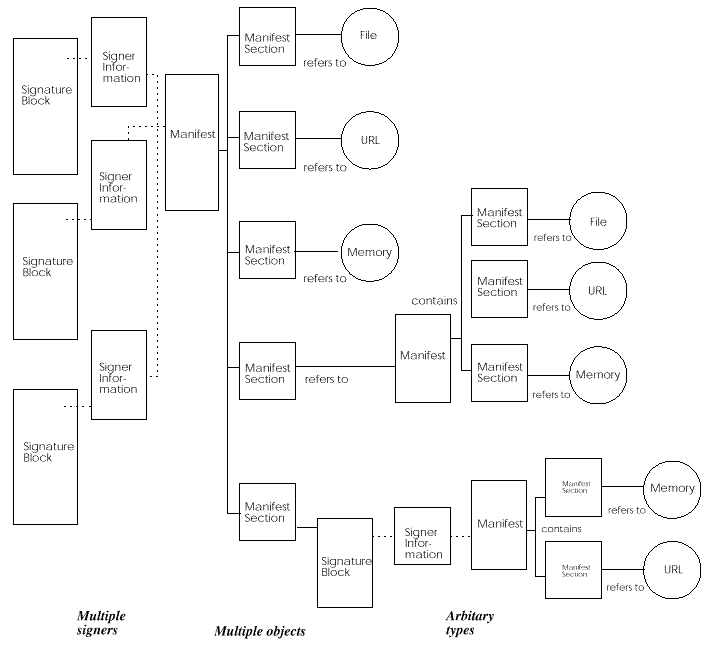
Figure: Signed Manifest Architectural View
The signed manifest is built from the following components:
-
The manifest describes a collection of digital objects. It
contains one or more manifest sections, where each section refers
to one of the objects within the collection of objects being described.
A section contains a reference to the object, attributes about the
object, a list of digest algorithm identifiers that were used to digest
the object, and a list of the associated digest values. The description
is human-readable.
-
The signer's information describes a list of references to one or
more sections of the manifest. Each reference includes a signature
information section which contains a reference to a manifest section, a
list of digest algorithms identifiers used to digest the manifest
section, a list of digest values for each specified algorithm
identifier, and any other attributes that the signer may wish to be
associated with the manifest section. It is possible for a signer to
sign only part of a manifest description. Using this structure, it is
possible to add signer-specific assertions or attributes to the object
being signed. This description is human-readable.
-
The signature block contains a signature over the signer's
information. The signature block is encoded in the particular format
required by the signature block representation, for example, for a
PKCS#7 signature block, the encoding format is BER/DER.
The relationship of these components is shown in
Relationships of Manifest, Signer's Info and Signature Block.
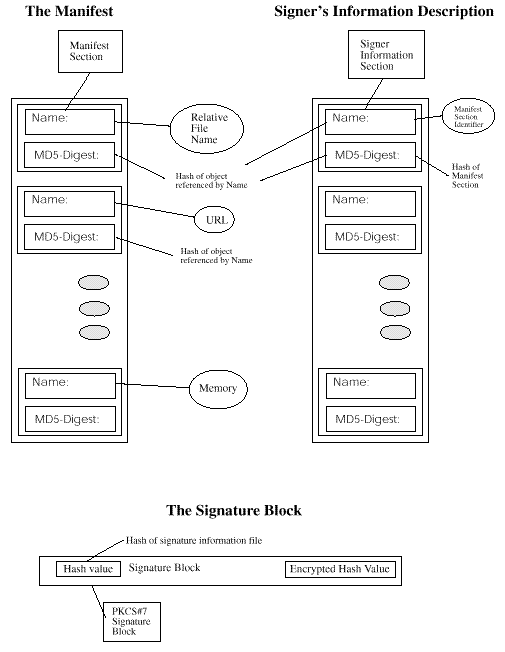
Figure: Relationships of Manifest, Signer's Info and Signature Block
These three objects must be zipped to form a single set of credentials.
Multiple implementations of standard zip algorithms
interoperate on one or more platforms, hence a zipped, signed
manifest retains a substantial degree of interoperability.
The format used to describe both the manifest and the signer's
information are a series of Name:Value pairs, (RFC 822). Binary data of
any form is represented in base64. Continuations are required for
binary data which causes line length to exceed 72 bytes. Examples of
binary data are digests and signatures.


