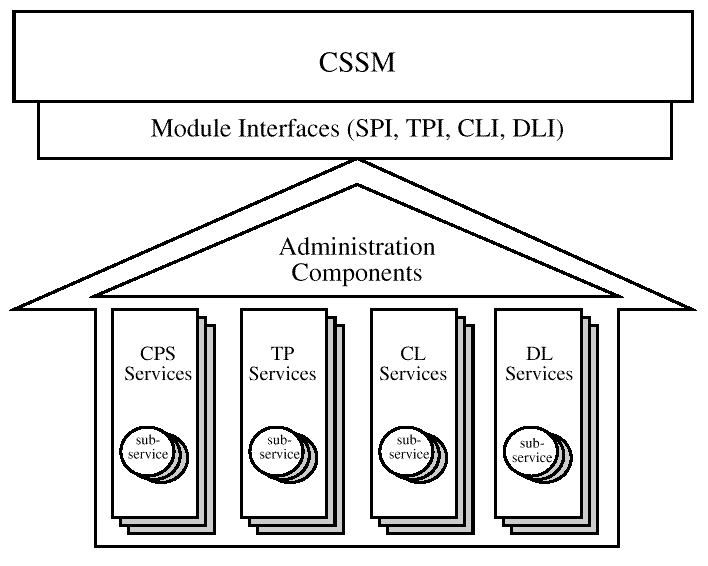

A CDSA add-in module is a dynamically-linkable library, composed of functions that implement some or all of the CSSM Module Interfaces. Add-in module functionality is partitioned into two areas:
Add-in modules provide one or more categories of security services to applications. The service categories are Cryptographic Service Provider (CSP) services, Trust Policy (TP) services, Certificate Library (CL) services, and Data Storage Library (DL) services. Each security service contains one or more implementation instances, called sub-services. For a CSP service providing access to hardware tokens, a sub-service would represent a slot. For a DL service provider, a sub-service would represent a type of persistent storage. These sub-services each support the module interface for their respective service categories. This documentation-part describes the module interface functions in the DL service category. More information about CSP services can be found in the CSSM Cryptographic Service Provider Interface Specification. More information about TP services can be found in the CSSM Trust Policy Interface Specification. More information about CL services can be found in the CSSM Certificate Library Interface Specification.
Each module, regardless of the security services it offers, has the same set of administrative responsibilities. Every module must expose functions which allow CSSM to indicate events such as module attach and detach. In addition, as part of the attach operation, every module must be able to verify its own integrity, verify the integrity of CSSM, and register with CSSM. Detailed information about add-in module structure, administration, and interfaces can be found in the CSSM Add-in Module Structure and Administration Specification.
The implementation of DL operations should be semantically free. For example, a DL operation which inserts a trusted X.509 certificate into a data store should not be responsible for verifying the trust on that certificate. The semantic interpretation of security objects should be implemented in TP services, layered services, and applications.
A pass-through function is defined in the DL API. This mechanism allows each DL to provide additional functions to store and retrieve certificates, CRLs and other security-related objects. Pass-through functions may be used to increase functionality or enhance performance.
| Contents | Next section | Index |