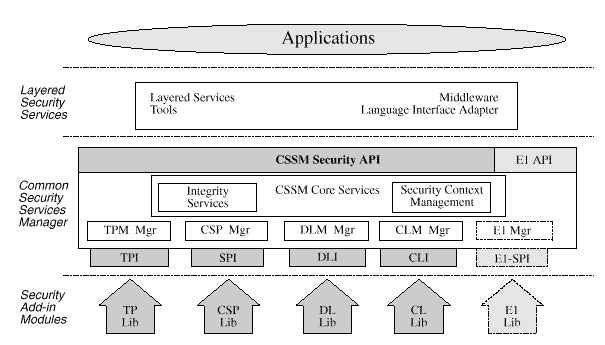
The Common Security Services Manager (CSSM) is the core of CDSA. CSSM manages categories of security services and multiple discrete implementations of those services as add-in security modules. CSSM:
Applications request security services through the CSSM security API or via layered security services and tools implemented over the CSSM API. The requested security services are performed by add-in security modules. Four basic types of module managers are defined:
Over time, new categories of security services may be defined, and new module managers may be required. CSSM supports elective module managers that dynamically extend the system with new categories of security services.
Below CSSM are add-in security modules that perform cryptographic operations, manipulate certificates, manage application-domain-specific trust policies, and perform new, elective categories of security services. Add-in security modules can be provided by independent software and hardware vendors as competitive products. Applications use CSSM module managers to direct their requests to add-in modules from specific vendors or to any add-in module that performs the required services. A single add-in module can provide one or more categories of service. Modules implementing more than one category of service are called multi-service modules.

CSSM core services support:
The module management functions are used by applications and by add-in modules to support module installation, registration of module features and attributes, and queries to retrieve information on module availability and features.
Security context management provides secured runtime caching of user-specific, cryptographic state information for use by multi-step cryptographic operations, such as staged hashing. These operations require multiple calls to a CSP and produce intermediate state that must be managed. CSSM manages this state information for the CSP, enabling more CSPs to easily support multiple concurrent callers.
The CSSM Embedded Integrity Services Library (EISL) provides secure verification services. CSSM, add-in modules, elective module managers, and optionally applications use EISL to verify the identity and integrity of components of CDSA. CSSM uses EISL functions to check dynamic components as they are added to the system. These components include: elective module managers, add-in service modules, and CSSM itself. In the future, applications will also be verified by CSSM before providing service to the application. The EISL services focus on detecting impostors or unauthorized components and tampering of authorized components.
| Contents | Next section | Index |