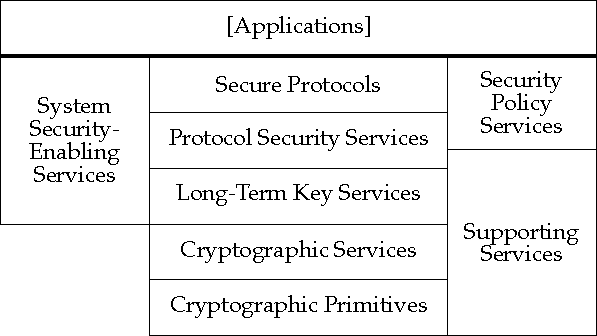
The PKI Architecture components are grouped into the following broad functional categories:

It is not anticipated that the Internet PKI will define any interfaces, protocols, profiles, or negotiation mechanisms in the area of system security-enabling services.
The PKI Task Group endorses use of the IETF PKIX operational protocols as the basis for standardization of the relevant PKI Architecture Public-Key Delivery and Verification protocols. These IETF PKIX specifications are:
The PKI Task Group recommends that the Key Recovery interface should be standardized and endorses the use of the CSSM Key Recovery API from CDSA, Version 2.0.
The PKI Task Group recommends that the Public-Key Delivery and Verification interfaces should be standardized. The PKI Task Group endorses the CSSM API from CDSA, Version 2.0 as the base document for this interface standard.
The PKI Task Group recommends that the following Certificate Management interfaces should be standardized at a minimum:
The PKI Task Group endorses the CSSM API from CDSA, Version 2.0 as the base document for this interface standard.
Specification of the Publication Authority interface would also be useful to providers of repositories and communications protocols who wish to make their products available as certificate and CRL transmission media; a standard Publication Authority interface would allow them to provide Publication Authority services without requiring changes to CA Agent code.
A policy profile for the Internet PKI environment has been published as IETF RFC 2527: Internet X.509 Public Key Infrastructure Certificate Policy and Certification Practices Framework.
In addition to these interfaces, the PKI Task Group recommends that interfaces for protection mechanism negotiation and privilege and delegation management should be standardized. The preferred interfaces for these services are IETF RFC 2478: The Simple and Protected GSSI Negotiation Mechanism and IETF CAT XGSS-API, respectively.
It is recommended that IETF RFC 2030: Simple Network Time Protocol (SNTP) is adopted as the time service protocol for use within the PKI Architecture.
It is recommended that IETF RFC 2251: Lightweight Directory Access Protocol, Version 3 (LDAPv3) is used as the basic directory service protocol within the PKI Architecture.
Components of the PKI Architecture will access time via the interface provided by the supporting operating system.
It is recommended that the C LDAP Application Program Interface is used as the interface to directory services.
| Contents | Next section | Index |