It is expected that this section will be revised in a future version of the PKI Architecture to reflect current work within The Open Group on biometric and other authentication devices in conjunction with PKI and SSO architectures.
The PKI Architecture is intended to support at least two kinds of hardware security device: security tokens and cryptographic modules.
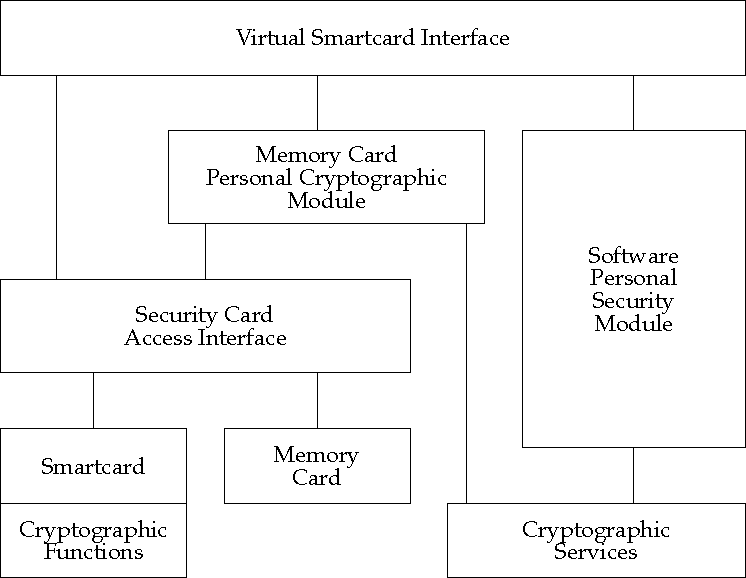
This class of device includes Smartcards, memory cards, time-synchronized tokens, and challenge-response tokens. These devices may provide cryptographic primitives and services, Virtual Smartcard services, and authentication functions.
Smartcards are assumed by the PKI Architecture to provide Virtual Smartcard services. They will also frequently also provide at least the key activation and signing components of cryptographic services; they may also provide other cryptographic services.
Memory cards provide only storage; Virtual Smartcard services involving state maintenance (for example, key activation) or cryptography will have to be provided by the memory card's software drivers.

Time-synchronized and challenge-response tokens provide only authentication functionality, and will typically be integrated into the PKI Architecture through modifications to the system security-enabling services (particularly the logon and obtain credentials components of those services).
This class of device includes chipsets, bus-connected cryptographic adaptors, and remote cryptographic servers providing cryptographic primitives and services, but not providing user authentication functions.
Cryptographic modules are assumed by the PKI Architecture to provide the full range of cryptographic services (and they may provide direct access to some cryptographic primitives for the convenience of designers of new cryptographic services).
| Contents | Next section | Index |