Two major categories of security services are cryptographic operations and certificate creation and manipulation.
System-wide policies governing availability and use of these services can be defined by:
For example, a site-wide administrator can require that the privacy mode (requiring encryption and decryption) in a communication service (such as Secure Sockets Layer) can only be used after 5:00 PM on Monday through Friday. This policy defines the extent of security services generally available to applications. Either the service is available to everyone or it is available to no one.
An example of controlling individual use of an available service is a government policy stating that financial applications can perform encryption and decryption with a key size greater than 56 effective bits.
CDSA defines a global, integrity-based policy for all CSSM systems. This policy is distinct from all locally defined system-wide policies. The CDSA integrity policy mandates the use of bilateral authentication when attaching add-in service modules and offers this option to applications. A complete description of this global policy, the mechanisms, and the interfaces used to implement it are described in the documents Common Data Security Architecture (CDSA) Specification, CSSM Application Programming Interface, and CSSM Add-in Module Structure and Administration Specification.
Policies are also defined by Trust Policy Modules (TPM) and add-in service modules. TPMs define and enforce policies over an application-specific domain. Enforcement is based on certificate verification. Add-in service modules define usage policies based on module capabilities presented in the module's signed manifest.
These four sources form a hierarchy of policy definition applied in the following order:
The policy applied to a particular application request is the ordered evaluation of these policy definitions.
CDSA, as defined in the Common Data Security Architecture (CDSA) Specification, defines when and how three of these policy definitions are evaluated. The Common Security Services Manager (CSSM), which is the core of CDSA, can be enhanced to support the specification and application of a local, system-wide policy, controlling the offering and use of security services.
Use of system-wide policy statements is not required and the CSSM mechanisms to support them are optional. Vendors can choose to provide these mechanisms in their products. These mechanisms can assist in making their products more full-featured and attractive to enterprise customers. It may also assist these product vendors to achieve compliance with import, export, or use restrictions imposed by a relevant government entity.
CDSA is intended to be the multi-platform security architecture that's horizontally broad and vertically robust.
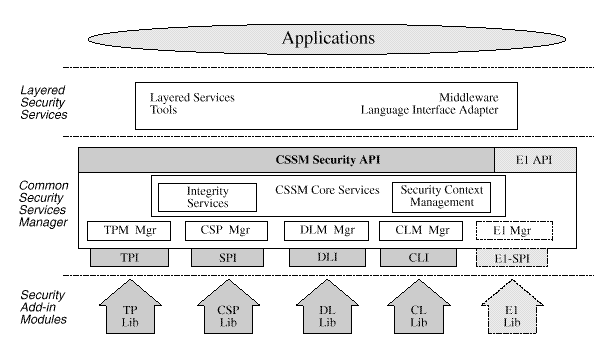
The Common Security Services Manager (CSSM) is the core of CDSA. CSSM manages categories of security services and multiple discrete implementations of those services as add-in security modules. CSSM:
Applications request security services through the CSSM security API or via layered security services and tools implemented over the CSSM API. The requested security services are performed by add-in security modules. Four basic types of module managers are defined:
Over time, new categories of security services will be defined, and new module managers will be required. CSSM supports elective module managers that dynamically extend the system with new categories of security services.
Below CSSM are add-in security modules that perform cryptographic operations, manipulate certificates, and manage application-domain-specific trust policies. Add-in security modules may be provided by independent software and hardware vendors as competitive products. Applications use CSSM to direct their requests to modules from specific vendors or to any module that performs the required services. Add-in modules augment the set of available security services.

| Contents | Next section | Index |