The CSP is always responsible for the secure storage of private keys. Optionally the CSP may assume responsibility for the secure storage of other object types, such as symmetric keys and certificates. The implementation of secured persistent storage for keys can use the services of a Data Storage Library module within the CSSM framework or some approach internal to the CSP. Accessing persistent objects managed by the CSP, other than keys, is performed using CSSM's Data Storage Library APIs.
CSPs optionally support a password-based login sequence. When login is supported, the caller is allowed to change passwords as deemed necessary. This is part of a standard user-initiated maintenance procedure. Some CSPs support operations for privileged, CSP administrators. The model for CSP administration varies widely among CSP implementations. For this reason, CSSM does not define APIs for vendor-specific CSP administration operations. CSP vendors can makes these services available to CSP administration tools using the CSSM_Passthrough function.
The range and types of cryptographic services a CSP supports is at the discretion of the vendor. A registry and query mechanism is available through the CSSM for CSPs to disclose the services and details about the services. As an example, a CSP may register with the CSSM: Encryption is supported, the algorithms present are DES with cipher block chaining for key sizes 40 and 56 bits, triple DES with 3 keys for key size 168 bits.
All cryptographic services requested by applications will be channeled to one of the CSPs via the CSSM. CSP vendors only need target their modules to CSSM for all security-conscious applications to have access to their product.
Calls made to a Cryptographic Service Provider (CSP) to perform cryptographic operations occur within a framework called a session, which is established and terminated by the application. The session context (simply referred to as the context is created prior to starting CSP operations and is deleted as soon as possible upon completion of the operation. Context information is not persistent; it is not saved permanently in a file or database.
Before an application calls a CSP to perform a cryptographic operation, the application uses the query services function to determine what CSPs are installed, and what services they provide. Based on this information, the application then can determine which CSP to use for subsequent operations; the application creates a session with this CSP and performs the operation.
Depending on the class of cryptographic operations, individualized attributes are available for the cryptographic context. Besides specifying an algorithm when creating the context, the application may also initialize a session key, pass an initialization vector and/or pass padding information to complete the description of the session. A successful return value from the create function indicates the desired CSP is available. Functions are also provided to manage the created context.
When a context is no longer required, the application calls CSSM_DeleteContext. Resources that were allocated for that context can be reclaimed by the operating system.
Cryptographic operations come in two types-a single call to perform an operation and a staged method of performing the operation. For the single call method, only one call is needed to obtain the result. For the staged method, there is an initialization call followed by one or more update calls, and ending with a completion (final) call. The result is available after the final function completes its execution for most crypto operations-staged encryption/decryption are an exception in that each update call generates a portion of the result.
The two PKI-based algorithms with wide spread usage are:
For RSA-based algorithms, CDSA adopts the PKCS#1 standard for key representation.
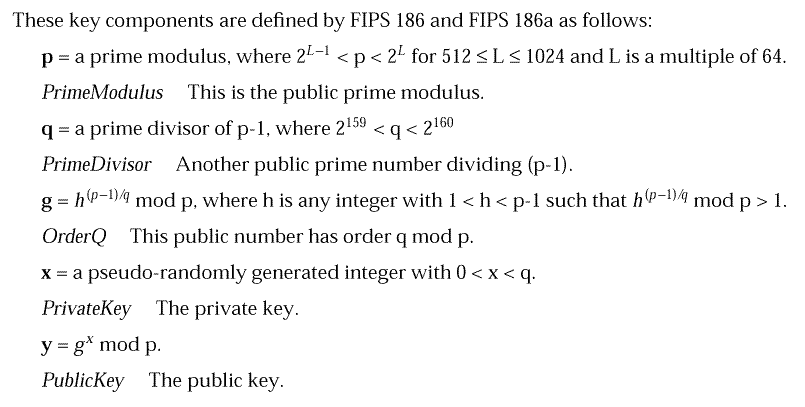
For DSA-based algorithms, no organization has published a standard and no de facto standard seems to exists. CDSA defines a standard representation for DSA key based on the DSA algorithm definitions in the FIPS 186 and FIPS 186a standards. Complete documentation on these standards can be found at http://csrc.ncsl.nist.gov/fips/fips186.txt and http://csrc.ncsl.nist.gov/fips/fips186a.txt respectively.
A DSA public key is represented as a BER-encoding of a sequence
list containing:
PrimeModulus; /* p */
PrimeDivisor; /* q */
OrderQ; /* g */
PublicKey; /* y */
A DSA private key is represented as a BER-encoded sequence list
containing:
PrimeModulus; /* p */
PrimeDivisor; /* q */
OrderQ; /* g */
PrivateKey; /* x */

This section describes the data structures which may be passed to or
returned from a CSP function. They will be used by applications to
prepare data to be passed as input parameters into CSSM API function
calls, that will be passed without modification to the appropriate
CSP. The CSP is then responsible for interpreting them and returning
the appropriate data structure to the calling application via CSSM.
These data structures are defined in the header file
typedef uint32 CSSM_CSP_HANDLE
/* Cryptographic Service Provider Handle */
typedef struct cssm_data{
uint32 Length; /* in bytes */
uint8 *Data;
} CSSM_DATA, *CSSM_DATA_PTR
typedef struct cssm_crypto_data {
CSSM_DATA_PTR Param;
CSSM_CALLBACK Callback;
uint32 CallbackID;
}CSSM_CRYPTO_DATA, *CSSM_CRYPTO_DATA_PTR
typedef struct cssm_date {
uint8 Year[4];
uint8 Month[2];
uint8 Day[2];
} CSSM_DATE, *CSSM_DATE_PTR;
typedef struct cssm_range {
uint32 Min; /* inclusive minimum value */
uint32 Max; /* inclusive maximum value */
} CSSM_RANGE, *CSSM_RANGE_PTR;
typedef struct cssm_query_size_data {
uint32 SizeInputBlock; /* Input data block size */
uint32 SizeOutputBlock; /* Output data block size */
} CSSM_QUERY_SIZE_DATA, *CSSM_QUERY_SIZE_DATA_PTR;
typedef uint32 CSSM_HEADERVERSION;
#define CSSM_KEYHEADER_VERSION (2)
typedef struct cssm_key_size {
uint32 KeySizeInBits; /* Key size in bits */
uint32 EffectiveKeySizeInBits; /* Effective key size in bits */
} CSSM_KEYSIZE, *CSSM_KEYSIZE_PTR;
typedef struct cssm_keyheader {
CSSM_HEADERVERSION HeaderVersion; /* Key header version */
CSSM_GUID CspId; /* GUID of CSP generating the key */
uint32 BlobType; /* See BlobType #define's */
uint32 Format; /* Raw or Reference format */
uint32 AlgorithmId; /* Algorithm ID of key */
uint32 KeyClass; /* Public/Private/Secret, etc. */
uint32 EffectiveKeySizeInBits; /* Size of logical
key/modulus/prime in bits */
uint32 KeyAttr; /* Attribute flags */
uint32 KeyUsage; /* Key use flags */
CSSM_DATE StartDate; /* Effective date of key */
CSSM_DATE EndDate; /* Expiration date of key */
uint32 WrapAlgorithmId; /* == CSSM_ALGID_NONE if clear key */
uint32 WrapMode; /* if alg supports multiple wrapping
modes */
uint32 Reserved;
} CSSM_KEYHEADER, *CSSM_KEYHEADER_PTR;
| Keyblob Type Identifier | Description |
|---|---|
| CSSM_KEYBLOB_RAW | The blob is a clear, raw key |
| CSSM_KEYBLOB_RAW_BERDER | The blob is a clear key, DER encoded |
| CSSM_KEYBLOB_REFERENCE | The blob is a reference to a key |
| CSSM_KEYBLOB_WRAPPED | The blob is a wrapped RAW key |
| CSSM_KEYBLOB_WRAPPED_BERDER | The blob is a wrapped DER encoded key |
| CSSM_KEYBLOB_OTHER | Other, CSP defined |
| Keyblob Format Identifier | Description |
|---|---|
| CSSM_KEYBLOB_RAW_FORMAT_NONE | Raw format is unknown |
| CSSM_KEYBLOB_RAW_FORMAT_PKCS1 | RSA PKCS1 V1.5 See "RSA Encryption Standard", an RSA Laboratories publication http://www.rsa.com/rsalabs/pubs/PKCS/ |
| CSSM_KEYBLOB_RAW_FORMAT_PKCS3 | RSA PKCS3 V1.5 See"Diffie-Hellman Key-Agreement Standard", an RSA Laboratories publication http://www.rsa.com/rsalabs/pubs/PKCS/ |
| CSSM_KEYBLOB_RAW_FORMAT_MSCAPI | Microsoft CAPI V2.0 |
| CSSM_KEYBLOB_RAW_FORMAT_PGP | PGP See "PGP Cryptographic Software Development Kit (PGP sdk)", a PGP Publication |
| CSSM_KEYBLOB_RAW_FORMAT_FIPS186 | US Gov. FIPS 186: DSS V |
| CSSM_KEYBLOB_RAW_FORMAT_BSAFE | RSA Bsafe V3.0 See "BSAFE, A Cryptographic Toolkit, Library Reference Manual", an RSA Data Security Inc. publication |
| CSSM_KEYBLOB_RAW_FORMAT_PKCS8 | RSA PKCS8 V1.2 See "Private-Key Information Syntax Standard", an RSA Laboratories publication http://www.rsa.com/rsalabs/pubs/PKCS/" |
| CSSM_KEYBLOB_RAW_FORMAT_PKCS11 | RSA PKCS11 V2.0 See "Cryptographic Token Interface Standard", an RSA Laboratories publication http://www.rsa.com/rsalabs/pubs/PKCS/ |
| CSSM_KEYBLOB_RAW_FORMAT_CDSA | CDSA format See this specification and CSSM Cryptographic Service Provider Interface Specification |
| CSSM_KEYBLOB_RAW_FORMAT_OTHER | Other, CSP defined |
| CSSM_KEYBLOB_REF_FORMAT_INTEGER | Reference is a number or handle |
| CSSM_KEYBLOB_REF_FORMAT_STRING | Reference is a string or name |
| CSSM_KEYBLOB_REF_FORMAT_OTHER | Reference is a CSP-defined format |
| Key Class Identifier | Description |
|---|---|
| CSSM_KEYCLASS_PUBLIC_KEY | Key is a public key |
| CSSM_KEYCLASS_PRIVATE_KEY | Key is a private key |
| CSSM_KEYCLASS_SESSION_KEY | Key is a session or symmetric key |
| CSSM_KEYCLASS_SECRET_PART | Key is part of secret key |
| CSSM_KEYCLASS_OTHER | Other |
| Attribute values valid only as inputs to functions and will never appear in a key header: | |
|---|---|
| Attribute | Description |
| CSSM_KEYATTR_RETURN_DEFAULT | Key is returned in CSP's default form. |
| CSSM_KEYATTR_RETURN_DATA | Key is returned with key bits present. The format of the returned key can be raw or wrapped. |
| CSSM_KEYATTR_RETURN_REF | Key is returned as a reference. |
| CSSM_KEYATTR_RETURN_NONE | Key is not returned. |
| Attribute values valid as inputs to functions and retained values in a key header: | |
| Attribute | Description |
| CSSM_KEYATTR_PERMANENT | Key is stored persistently in the CSP, such asa PKCS11 token object. |
| CSSM_KEYATTR_PRIVATE | Key is a private object and protected by either a user login, a password, or both. |
| CSSM_KEYATTR_MODIFIABLE | The key or its attributes can be modified. |
| CSSM_KEYATTR_SENSITIVE | Key is sensitive. It may only be extracted from the CSP in a wrapped state. |
| CSSM_KEYATTR_EXTRACTABLE | Key is extractable from the CSP. If this bit is not set, either the key is not stored in the CSP, or it cannot be extracted under any circumstances. |
| Attribute values valid in a key header when set by a CSP: | |
| Attribute | Description |
| CSSM_KEYATTR_ALWAYS_SENSITIVE | Key has always been sensitive. |
| CSSM_KEYATTR_NEVER_EXTRACTABLE | Key has never been extractable. |
| Usage Mask | Description |
|---|---|
| CSSM_KEYUSE_ANY | Key may be used for any purpose supported by the algorithm. |
| CSSM_KEYUSE_ENCRYPT | Key may be used for encryption. |
| CSSM_KEYUSE_DECRYPT | Key may be used for decryption. |
| CSSM_KEYUSE_SIGN | Key can be used to generate signatures. For symmetric keys this represents the ability to generate MACs. |
| CSSM_KEYUSE_VERIFY | Key can be used to verify signatures. For symmetric keys this represents the ability to verify MACs. |
| CSSM_KEYUSE_SIGN_RECOVER | Key can be used to perform signatures with message recovery. This form of a signature is generated using the CSSM_EncryptData API with the algorithm mode set to CSSM_ALGMODE_PRIVATE_KEY |
| CSSM_KEYUSE_VERIFY_RECOVER | Key can be used to verify signatures with message recovery. This form of a signature verified using the CSSM_DecryptData API with the algorithm mode set to CSSM_ALGMODE_PUBLIC_KEY. |
| CSSM_KEYUSE_WRAP | Key can be used to wrap another key. |
| CSSM_KEYUSE_UNWRAP | Key can be used to unwrap a key. |
| CSSM_KEYUSE_DERIVE | Key can be used as the source for deriving other keys. |
| Attribute Name | Pertains to the Application's local copy of the key | Pertains to the CSP-stored copy of the key |
|---|---|---|
| BlobType | X | |
| Format | X | |
| AlgorithmId | X | X |
| KeyClass | X | X |
| EffectiveKeySizeInBits | X | X |
| KeyAttr | Only the flag bits RETURN_XXX | All the flag bits except RETURN_XXX |
| KeyUsage | X | X |
| StartDate | X | X |
| EndDate | X | X |
| WrapAlgorithmId | X | |
| WrapMode | X |
typedef struct cssm_key {
CSSM_KEYHEADER KeyHeader; /* Fixed length key header */
CSSM_DATA KeyData; /* Variable length key data */
} CSSM_KEY, *CSSM_KEY_PTR;
typedef CSSM_KEY CSSM_WRAP_KEY, *CSSM_WRAP_KEY_PTR;
typedef CSSM_DATA_PTR (CSSMAPI *CSSM_CALLBACK)
(void *allocRef, uint32 ID);
typedef enum cssm_csptype {
CSSM_CSP_SOFTWARE = 1,
CSSM_CSP_HARDWARE = CSSM_CSP_SOFTWARE+1,
CSSM_CSP_HYBRID = CSSM_CSP_SOFTWARE+2,
}CSSM_CSPTYPE;
#define CSSM_CSP_SESSION_EXCLUSIVE 0x0001
/* single user CSP */
#define CSSM_CSP_SESSION_READWRITE 0x0002
/* caller can read and write objects such as keys in the CSP */
#define CSSM_CSP_SESSION_SERIAL 0x0004
/* multi-user, re-entrant CSP that requires serial access */
typedef CSSM_RETURN (CSSMAPI *CSSM_NOTIFY_CALLBACK)
(CSSM_CSP_HANDLE ModuleHandle,
uint32 Application,
uint32 Reason,
void* Param)
#define CSSM_NOTIFY_SURRENDER 0
#define CSSM_NOTIFY_COMPLETE 1
#define CSSM_NOTIFY_DEVICE_REMOVED 2
#define CSSM_NOTIFY_DEVICE_INSERTED 3
typedef struct cssm_handleinfo {
uint32 SlotID;
uint32 SessionFlags;
CSSM_NOTIFY_CALLBACK Callback;
uint32 ApplicationContext;
} CSSM_HANDLEINFO, *CSSM_HANDLEINFO_PTR;
typedef enum cssm_padding {
CSSM_PADDING_NONE = 0,
CSSM_PADDING_CUSTOM = CSSM_PADDING_NONE+1,
CSSM_PADDING_ZERO = CSSM_PADDING_NONE+2,
CSSM_PADDING_ONE = CSSM_PADDING_NONE+3,
CSSM_PADDING_ALTERNATE = CSSM_PADDING_NONE+4,
CSSM_PADDING_FF = CSSM_PADDING_NONE+5,
CSSM_PADDING_PKCS5 = CSSM_PADDING_NONE+6,
CSSM_PADDING_PKCS7 = CSSM_PADDING_NONE+7,
CSSM_PADDING_CipherStealing = CSSM_PADDING_NONE+8,
CSSM_PADDING_RANDOM = CSSM_PADDING_NONE+9,
} CSSM_PADDING;
typedef struct cssm_context_attribute{
uint32 AttributeType;
uint32 AttributeLength;
union cssm_context_attribute_value {
char *String;
uint32 Uint32;
CSSM_CRYPTO_DATA_PTR Crypto;
CSSM_KEY_PTR Key;
CSSM_DATA_PTR Data;
CSSM_DATE_PTR Date;
CSSM_RANGE_PTR Range;
CSSM_VERSION_PTR Version;
} Attribute;
} CSSM_CONTEXT_ATTRIBUTE, *CSSM_CONTEXT_ATTRIBUTE_PTR;
| Value | Description | Data Type |
|---|---|---|
| CSSM_ATTRIBUTE_NONE | No attribute | None |
| CSSM_ATTRIBUTE_CUSTOM | Custom data | Opaque pointer |
| CSSM_ATTRIBUTE_DESCRIPTION | Description of attribute | String |
| CSSM_ATTRIBUTE_KEY | Key Data | CSSM_KEY |
| CSSM_ATTRIBUTE_INIT_VECTOR | Initialization vector | CSSM_DATA |
| CSSM_ATTRIBUTE_SALT | Salt | CSSM_DATA |
| CSSM_ATTRIBUTE_PADDING | Padding information | CSSM_PADDING |
| CSSM_ATTRIBUTE_RANDOM | Random data | CSSM_DATA |
| CSSM_ATTRIBUTE_SEED | Seed | CSSM_CRYPTO_DATA |
| CSSM_ATTRIBUTE_PASSPHRASE | Pass phrase | CSSM_CRYPTO_DATA |
| CSSM_ATTRIBUTE_KEY_LENGTH | Key length specified in bits | uint32 |
| CSSM_ATTRIBUTE_KEY_LENGTH_RANGE | Key length range specified in bits | CSSM_RANGE |
| CSSM_ATTRIBUTE_BLOCK_SIZE | Block size | uint32 |
| CSSM_ATTRIBUTE_OUTPUT_SIZE | Output size | uint32 |
| CSSM_ATTRIBUTE_ROUNDS | Number of runs or rounds | uint32 |
| CSSM_ATTRIBUTE_IV_SIZE | Size of initialization vector | uint32 |
| CSSM_ATTRIBUTE_ALG_PARAMS | Algorithm parameters | CSSM_DATA |
| CSSM_ATTRIBUTE_LABEL | Label placed on an object when it is created | CSSM_DATA |
| CSSM_ATTRIBUTE_KEY_TYPE | Type of key to generate or derive | uint32 |
| CSSM_ATTRIBUTE_MODE | Algorithm mode to use for encryption | uint32 |
| CSSM_ATTRIBUTE_EFFECTIVE_BITS | Number of effective bits used in the RC2 cipher | uint32 |
| CSSM_ATTRIBUTE_START_DATE | Starting date for an object's validity | CSSM_DATE |
| CSSM_ATTRIBUTE_END_DATE | Ending date for an object's validity | CSSM_DATE |
| CSSM_ATTRIBUTE_KEYUSAGE | Usage restriction on the key | uint32 |
| CSSM_ATTRIBUTE_KEYATTR | Key attribute | uint32 |
| CSSM_ATTRIBUTE_VERSION | Version number | CSSM_VERSION |
| CSSM_ATTRIBUTE_PRIME | Prime value | CSSM_DATA |
| CSSM_ATTRIBUTE_BASE | Base Value | CSSM_DATA |
| CSSM_ATTRIBUTE_SUBPRIME | Subprime Value | CSSM_DATA |
| CSSM_ATTRIBUTE_ALG_ID | Algorithm identifier | uint32 |
| CSSM_ATTRIBUTE_ITERATION_COUNT | Algorithm iterations | uint32 |
| CSSM_ATTRIBUTE_ROUNDS_RANGE | Range of number of rounds possible | CSSM_RANGE |
The data referenced by a CSSM_ATTRIBUTE_CUSTOM attribute must be a single continuous memory block. This allows the CSSM to appropriately release all dynamically allocated memory resources.
typedef uint32 CSSM_CC_HANDLE /* Cryptographic Context Handle */
typedef struct cssm_context {
uint32 ContextType; /* context type */
uint32 AlgorithmType; /* algorithm type of context */
uint32 Reserve; /* reserved for future use */
uint32 NumberOfAttributes; /* number of attributes associated
with context */
CSSM_CONTEXT_ATTRIBUTE_PTR ContextAttributes; /* pointer to
attributes */
} CSSM_CONTEXT, *CSSM_CONTEXT_PTR;
| Value | Description |
|---|---|
| CSSM_ALGCLASS_NONE | Null Context type |
| CSSM_ALGCLASS_CUSTOM | Custom Algorithms |
| CSSM_ALGCLASS_KEYEXCH | Key Exchange Algorithms |
| CSSM_ALGCLASS_SIGNATURE | Signature Algorithms |
| CSSM_ALGCLASS_SYMMETRIC | Symmetric Encryption Algorithms |
| CSSM_ALGCLASS_DIGEST | Message Digest Algorithms |
| CSSM_ALGCLASS_RANDOMGEN | Random Number Generation Algorithms |
| CSSM_ALGCLASS_UNIQUEGEN | Unique ID Generation Algorithms |
| CSSM_ALGCLASS_MAC | Message Authentication Code Algorithms |
| CSSM_ALGCLASS_ASYMMETRIC | Asymmetric Encryption Algorithms |
| CSSM_ALGCLASS_KEYGEN | Key Generation Algorithms |
| CSSM_ALGCLASS_DERIVEKEY | Key Derivation Algorithms |
| Value | Description |
|---|---|
| CSSM_ALGID_NONE | Null algorithm |
| CSSM_ALGID_CUSTOM | Custom algorithm |
| CSSM_ALGID_DH | Diffie Hellman key exchange algorithm |
| CSSM_ALGID_PH | Pohlig Hellman key exchange algorithm |
| CSSM_ALGID_KEA | Key Exchange Algorithm |
| CSSM_ALGID_MD2 | MD2 hash algorithm |
| CSSM_ALGID_MD4 | MD4 hash algorithm |
| CSSM_ALGID_MD5 | MD5 hash algorithm |
| CSSM_ALGID_SHA1 | Secure Hash Algorithm |
| CSSM_ALGID_NHASH | N-Hash algorithm |
| CSSM_ALGID_HAVAL | HAVAL hash algorithm (MD5 variant) |
| CSSM_ALGID_RIPEMD | RIPE-MD hash algorithm (MD4 variant developed for the European Community's RIPE project) |
| CSSM_ALGID_IBCHASH | IBC-Hash (keyed hash algorithm or MAC) |
| CSSM_ALGID_RIPEMAC | RIPE-MAC |
| CSSM_ALGID_HASHwithHitachi | Hitachi hash algorithm |
| CSSM_ALGID_DES | Data Encryption Standard block cipher |
| CSSM_ALGID_DESX | DESX block cipher (DES variant from RSA) |
| CSSM_ALGID_RDES | RDES block cipher (DES variant) |
| CSSM_ALGID_3DES_3KEY | Triple-DES block cipher (with 3 keys) |
| CSSM_ALGID_3DES_2KEY | Triple-DES block cipher (with 2 keys) |
| CSSM_ALGID_3DES_1KEY | Triple-DES block cipher (with 1 key) |
| CSSM_ALGID_IDEA | IDEA block cipher |
| CSSM_ALGID_RC2 | RC2 block cipher |
| CSSM_ALGID_RC5 | RC5 block cipher |
| CSSM_ALGID_RC4 | RC4 stream cipher |
| CSSM_ALGID_SEAL | SEAL stream cipher |
| CSSM_ALGID_CAST | CAST block cipher |
| CSSM_ALGID_BLOWFISH | BLOWFISH block cipher |
| CSSM_ALGID_SKIPJACK | Skipjack block cipher |
| CSSM_ALGID_LUCIFER | Lucifer block cipher |
| CSSM_ALGID_MADRYGA | Madryga block cipher |
| CSSM_ALGID_FEAL | FEAL block cipher |
| CSSM_ALGID_REDOC | REDOC 2 block cipher |
| CSSM_ALGID_REDOC3 | REDOC 3 block cipher |
| CSSM_ALGID_LOKI | LOKI block cipher |
| CSSM_ALGID_KHUFU | KHUFU block cipher |
| CSSM_ALGID_KHAFRE | KHAFRE block cipher |
| CSSM_ALGID_MMB | MMB block cipher (IDEA variant) |
| CSSM_ALGID_GOST | GOST block cipher |
| CSSM_ALGID_SAFER | SAFER K-40, K-64, K-128 block cipher |
| CSSM_ALGID_CRAB | CRAB block cipher |
| CSSM_ALGID_MULTI2 | MULTI2 block cipher algorithm (MULTI variant from Hitachi) |
| CSSM_ALGID_RSA | RSA public key cipher |
| CSSM_ALGID_CIPHERwithHitachiECCS | Hitachi's public key cipher algorithm with Elliptic Curve Cryptosystems |
| CSSM_ALGID_DSA | Digital Signature Algorithm |
| CSSM_ALGID_MD5WithRSA | MD5/RSA signature algorithm |
| CSSM_ALGID_MD2WithRSA | MD2/RSA signature algorithm |
| CSSM_ALGID_SIGwithHitachiECCS | Hitachi's signature algorithm with Elliptic Curve Cryptosystems |
| CSSM_ALGID_ElGamal | ElGamal signature algorithm |
| CSSM_ALGID_MD2Random | MD2-based random numbers |
| CSSM_ALGID_MD5Random | MD5-based random numbers |
| CSSM_ALGID_SHARandom | SHA-based random numbers |
| CSSM_ALGID_DESRandom | DES-based random numbers |
| CSSM_ALGID_MULTI2Random | MULTI2-based random numbers |
| CSSM_ALGID_SHA1WithRSA | SHA-1/RSA signature algorithm |
| CSSM_ALGID_RSA_PKCS | RSA as specified in PKCS #1 |
| CSSM_ALGID_RSA_ISO9796 | RSA as specified in ISO 9796 |
| CSSM_ALGID_RSA_RAW | Raw RSA as assumed in X.509 |
| CSSM_ALGID_CDMF | CDMF block cipher |
| CSSM_ALGID_CAST3 | Entrust's CAST3 block cipher |
| CSSM_ALGID_CAST5 | Entrust's CAST5 block cipher |
| CSSM_ALGID_GenericSecret | Generic secret operations |
| CSSM_ALGID_ConcatBaseAndKey | Concatenate two keys, base key first |
| CSSM_ALGID_ConcatKeyAndBase | Concatenate two keys, base key last |
| CSSM_ALGID_ConcatBaseAndData | Concatenate base key and random data, key first |
| CSSM_ALGID_ConcatDataAndBase | Concatenate base key and data, data first |
| CSSM_ALGID_XORBaseAndData | XOR a byte string with the base key |
| CSSM_ALGID_ExtractFromKey | Extract a key from base key, starting at arbitrary bit position |
| CSSM_ALGID_SSL3PreMasterGen | Generate a 48 byte SSL 3 pre-master key |
| CSSM_ALGID_SSL3MasterDerive | Derive an SSL 3 key from a pre-master key |
| CSSM_ALGID_SSL3KeyAndMacDerive | Derive the keys and MACing keys for the SSL cipher suite |
| CSSM_ALGID_SSL3MD5_MAC | Performs SSL 3 MD5 MACing |
| CSSM_ALGID_SSL3SHA1_MAC | Performs SSL 3 SHA-1 MACing |
| CSSM_ALGID_MD5_PBE | Generate key by MD5 hashing a base key |
| CSSM_ALGID_MD2_PBE | Generate key by MD2 hashing a base key |
| CSSM_ALGID_SHA1_PBE | Generate key by SHA-1 hashing a base key |
| CSSM_ALGID_WrapLynks | Spyrus LYNKS DES based wrapping scheme w/checksum |
| CSSM_ALGID_WrapSET_OAEP | SET key wrapping |
| CSSM_ALGID_BATON | Fortezza BATON cipher |
| CSSM_ALGID_ECDSA | Elliptic Curve DSA |
| CSSM_ALGID_MAYFLY | Fortezza MAYFLY cipher |
| CSSM_ALGID_JUNIPER | Fortezza JUNIPER cipher |
| CSSM_ALGID_FASTHASH | Fortezza FASTHASH |
| CSSM_ALGID_3DES | Generix 3DES |
| CSSM_ALGID_SSL3MD5 | SSL3 with MD5 |
| CSSM_ALGID_SSL3SHA1 | SSL3 with SHA1 |
| CSSM_ALGID_FortezzaTimestamp | Fortezza with Timestamp |
| CSSM_ALGID_SHA1WithDSA | SHA1 with DSA |
| CSSM_ALGID_SHA1WithECDSA | SHA1 with Elliptic Curve DSA |
| CSSM_ALGID_DSA_BSAFE | DSA with BSAFE Key format |
| CSSM_ALGID_Bcrypt | BSI algorithm |
| CSSM_ALGID_LUCpkcds | LUC Public key crypto and Dig Sig Alg |
| CSSM_ALGID_BARAS | |
| CSSM_ALGID_SxalMbal | Substitution Xor Alg / Multi Block Alg |
| CSSM_ALGID_MISTY1 | Block Cipher |
| CSSM_ALGID_ENCRIP |
Some of the above algorithms operate in a variety of modes. The desired mode is specified using an attribute of type CSSM_ATTRIBUTE_MODE. The valid values for the mode attribute are as follows:
| Value | Description |
|---|---|
| CSSM_ALGMODE_NONE | Null Algorithm mode |
| CSSM_ALGMODE_CUSTOM | Custom mode |
| CSSM_ALGMODE_ECB | Electronic Code Book |
| CSSM_ALGMODE_ECBPad | ECB with padding |
| CSSM_ALGMODE_CBC | Cipher Block Chaining |
| CSSM_ALGMODE_CBC_IV8 | CBC with Initialization Vector of 8 bytes |
| CSSM_ALGMODE_CBCPadIV8 | CBC with padding and Initialization Vector of 8 bytes |
| CSSM_ALGMODE_CFB | Cipher FeedBack |
| CSSM_ALGMODE_CFB_IV8 | CFB with Initialization Vector of 8 bytes |
| CSSM_ALGMODE_CFBPadIV8 | CFB with Initialization Vector of 8 bytes and padding |
| CSSM_ALGMODE_OFB | Output FeedBack |
| CSSM_ALGMODE_OFB_IV8 | OFB with Initialization Vector of 8 bytes |
| CSSM_ALGMODE_OFBPadIV8 | OFB with Initialization Vector of 8 bytes and padding |
| CSSM_ALGMODE_COUNTER | Counter |
| CSSM_ALGMODE_BC | Block Chaining |
| CSSM_ALGMODE_PCBC | Propagating CBC |
| CSSM_ALGMODE_CBCC | CBC with Checksum |
| CSSM_ALGMODE_OFBNLF | OFB with NonLinear Function |
| CSSM_ALGMODE_PBC | Plaintext Block Chaining |
| CSSM_ALGMODE_PFB | Plaintext FeedBack |
| CSSM_ALGMODE_CBCPD | CBC of Plaintext Difference |
| CSSM_ALGMODE_PUBLIC_KEY | Use the public key |
| CSSM_ALGMODE_PRIVATE_KEY | Use the private key |
| CSSM_ALGMODE_SHUFFLE | Fortezza shuffle mode |
| CSSM_ALGMODE_ECB64 | Electronic Code Book 64 bits |
| CSSM_ALGMODE_CBC64 | Cipher BlockChaining 64 bits |
| CSSM_ALGMODE_OFB64 | Output Feedback 64 bits |
| CSSM_ALGMODE_CBC64 | Cipher Feedback 64 bits |
| CSSM_ALGMODE_CBC32 | Cipher Feedback 32 bits |
| CSSM_ALGMODE_CBC16 | Cipher Feedback 16 bits |
| CSSM_ALGMODE_CBC8 | Cipher Feedback 8 bits |
| CSSM_ALGMODE_WRAP | |
| CSSM_ALGMODE_PRIVATE_WRAP | |
| CSSM_ALGMODE_RELAYX | |
| CSSM_ALGMODE_ECB128 | Electronic Code Book 128 bits |
| CSSM_ALGMODE_ECB96 | Electronic Code Book 96 bits |
| CSSM_ALGMODE_CBC128 | Cipher Block Chaining 128 bits |
| CSSM_ALGMODE_OAEP_HASH | Algorithm mode for SET key wrapping |
typedef CSSM_CONTEXT CSSM_CSP_CAPABILITY, *CSSM_CSP_CAPABILITY_PTR;
typedef struct cssm_software_cspsubservice_info {
uint32 NumberOfCapabilities;
CSSM_CSP_CAPABILITY_PTR CapabilityList;
uint32 Reserved;
} CSSM_SOFTWARE_CSPSUBSERVICE_INFO,
*CSSM_SOFTWARE_CSPSUBSERVICE_INFO_PTR;
typedef struct cssm_hardware_cspsubservice_info {
uint32 NubmerOfCapabilities;
CSSM_CSP_CAPABILITY_PTR CapabilityList;
void* Reserved;
/* Reader/Slot Info */
char *ReaderDescription;
char *ReaderVendor;
char *ReaderSerialNumber;
CSSM_VERSION ReaderHardwareVersion;
CSSM_VERSION ReaderFirmwareVersion;
uint32 ReaderFlags;
uint32 ReaderCustomFlags;
char *TokenDescription;
char *TokenVendor;
char *TokenSerialNumber;
CSSM_VERSION TokenHardwareVersion;
CSSM_VERSION TokenFirmwareVersion;
uint32 TokenFlags;
uint32 TokenCustomFlags;
uint32 TokenMaxSessionCount;
uint32 TokenOpenedSessionCount;
uint32 TokenMaxRWSessionCount;
uint32 TokenOpenedRWSessionCount;
uint32 TokenTotalPublicMem;
uint32 TokenFreePublicMem;
uint32 TokenTotalPrivateMem;
uint32 TokenFreePrivateMem;
uint32 TokenMaxPinLen;
uint32 TokenMinPinLen;
char TokenUTCTime[16];
CSSM_STRING UserLabel;
CSSM_DATA UserCACertificate;
} CSSM_HARDWARE_CSPSUBSERVICE_INFO, *CSSM_HARDWARE_CSPSUBSERVICE_INFO_PTR;
| Reader Flag | Description |
|---|---|
| CSSM_CSP_RDR_TOKENPRESENT | Token is present in the reader |
| CSSM_CSP_RDR_TOKENREMOVABLE | Reader supports removable tokens |
| CSSM_CSP_RDR_HW | Reader is a hardware device |
The following fields may not be valid if the CSSM_CSP_RDR_TOKENPRESENT flag is not set in the ReaderFlags field. Unknown string and CSSM_DATA fields will be set to NULL, integer and date fields will be set t zero and flag fields will have all flags set to false.
| Token Flags | Description |
|---|---|
| CSSM_CSP_TOK_RNG | Token has random number generator |
| CSSM_CSP_TOK_WRITE_PROTECTED | Token is write protected |
| CSSM_CSP_TOK_LOGIN_REQUIRED | User must login to access private objects |
| CSSM_CSP_TOK_USER_PIN_INITIALIZED | User's PIN has been initialized |
| CSSM_CSP_TOK_EXCLUSIVE_SESSION | An exclusive session currently exists |
| CSSM_CSP_TOK_CLOCK_EXISTS | Token has built in clock |
| CSSM_CSP_TOK_ASYNC_SESSION | Token supports asynchronous operations |
| CSSM_CSP_TOK_PROT_AUTHENTICATION | Token has protected authentication path |
| CSSM_CSP_TOK_DUAL_CRYPTO_OPS | Token supports dual cryptographic operations |
CSSM_HARDWARE_CSPSUBSERVICE_INFO, *CSSM_HARDWARE_CSPSUBSERVICE_INFO_PTR;
typedef struct cssm_csp_wrappedproductinfo {
CSSM_VERSION StandardVersion;
CSSM_STRING StandardDescription;
CSSM_VERSION ProductVersion;
CSSM_STRING ProductDescription;
CSSM_STRING ProductVendor;
uint32 ProductFlags;
uint32 ProductCustomFlags;
} CSSM_CSP_WRAPPEDPRODUCTINFO, *CSSM_CSP_WRAPPEDPRODUCTINFO_PTR;
typedef uint32 CSSM_CSP_FLAGS;
#define CSSM_CSP_STORES_PRIVATE_KEYS
#define CSSM_CSP_STORES_PUBLIC_KEYS
#define CSSM_CSP_STORES_SESSION_KEYS
typedef struct cssm_cspsubservice {
uint32 SubServiceId;
CSSM_STRING Description;
CSSM_CSP_FLAGS CspFlags;
uint32 CspCustomFlags;
uint32 AccessFlags;
CSSM_CSP_TYPE CspType;
union cssm_subservice_info {
CSSM_SOFTWARE_CSPSUBSERVICE_INFO SoftwareCspSubService;
CSSM_HARDWARE_CSPSUBSERVICE_INFO HardwareCspSubService;
CSSM_HYBRID_CSPSUBSERVICE_INFO HybridCspSubService;
} SubserviceInfo;
CSSM_CSP_WRAPPEDPRODUCTINFO WrappedProduct;
} CSSM_CSPSUBSERVICE, *CSSM_CSPSUBSERVICE_PTR;
| CSP Information Structure Identifier | Structure Type |
|---|---|
| CSSM_CSP_TYPE_SOFTWARE | CSSM_SOFTWARE_CSPSUBSERVICE_INFO |
| CSSM_CSP_TYPE_HARDWARE | CSSM_HARDWARE_CSPSUBSERVICE_INFO |
typedef struct cssm_serviceinfo {
CSSM_STRING Description; /* Service description */
CSSM_SERVICE_TYPE Type; /* Service type */
CSSM_SERVICE_FLAGS Flags; /* Service flags */
uint32 NumberOfSubServices; /* Number of sub services in
SubService List */
union cssm_subservice_list {
void *SubServiceList;
CSSM_CSPSUBSERVICE_PTR CspSubServiceList;
CSSM_DLSUBSERVICE_PTR DlSubServiceList;
CSSM_CLSUBSERVICE_PTR ClSubServiceList;
CSSM_TPSUBSERVICE_PTR TpSubServiceList;
} SubServiceList;
void *Reserved;
} CSSM_SERVICE_INFO, *CSSM_SERVICE_INFO_PTR;
typedef struct cssm_moduleinfo {
CSSM_VERSION Version; /* Module version */
CSSM_VERSION CompatibleCSSMVersion; /* CSSM version the
module is written for*/
CSSM_GUID_PTR InterfaceGUID; /* opt GUID defining supported
interface */
CSSM_STRING Description; /* Module description */
CSSM_STRING Vendor; /* Vendor name */
CSSM_MODULE_FLAGS Flags; /* Flags to describe and
control module use */
CSSM_KEY_PTR AppAuthenRootKeys; /* Module-specific keys
to authenticate apps */
uint32 NumberOfAppAuthenRootKeys; /* Number of module-specific
root keys */
CSSM_SERVICE_MASK ServiceMask; /* Bit mask of supported
services */
uint32 NumberOfServices; /* Number of services in
ServiceList */
CSSM_SERVICE_INFO_PTR ServiceList; /* A list of service info
structures */
void *Reserved;
} CSSM_MODULE_INFO, *CSSM_MODULE_INFO_PTR;
The manpages for Cryptographic Operations can be found at the end of this chapter.
CSP developers may also define their own module-specific error codes, as described in CSSM Add-in Module Structure and Administration Specification.
The manpages for Extensibility Functions can be found at the end of this chapter.
The manpages for Module Management Functions can be found at the end of this chapter.
| Contents | Next section | Index |