-
-
Manifest-Version: 2.0
Name: pictures/ocean.gif
SectionName: Ocean picture
Digest_Algorithms: MD5
MD5-Digest: base64(md5-hash of ocean.gif)
Name: audio/ocean.au
SectionName: Ocean Sounds Audio File
Digest_Algorithms: MD5 SHA1
MD5-Digest: base64(md5-hash of ocean.au)
SHA1-Digest: base64(sha1-hash of ocean.au)
The signer's information description:
-
-
Signature-Version: 2.0
Name: audio/ocean.au
SectionName: Ocean Sounds Audio File
Digest_Algorithms: MD5
MD5-Digest: base64(MD5 Digest of manifest section entitled "Ocean Sounds")
The signature block is not shown here, but it would be represented as an ANS.1 encoded PKCS#7 signature block.
Note that the manifest includes two digests for audio/ocean.au, and the signer's information includes only one. At verification time the manifest section that is hashed is treated as opaque data; hence SHA1 digest is included in the hash.
-
-
Manifest-Version: 2.0
Name: SomeCompany.cert
SectionName: Trusted Root Certificate
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: http://www.stockquote.com
SectionName: Dynamic Stock Quote Service
DublinCore-Format: message/x-pkcs7
MAGIC: UsesMetaData
Integrity-TrustedSigner: Trusted Root Certificate
Trusted signer specifies the key holder that must have signed the dynamic object. The manifest section entitled "Trusted Root Certificate" contains a referent to a file where the trusted signer's certificate resides. The integrity of the Trusted Root Certificate is specified by including the hash value of the actual certificate in the manifest. This verifies the identity of the signer.
In this example, the signer has signed all sections of the manifest.
The signer's information description appears as follows:
-
-
Signature-Version: 2.0
Name: SomeCompany.cert
Digest_Algorithms: MD5
MD5-Digest: xxxx
Name: http://www.stockquote.com
Digest_Algorithms: MD5
MD5-Digest: xxxx
The PKCS#7 signature block is not shown.
-
-
Manifest-Version: 2.0
Name: ExamplePKCS7Data.pk7
SectionName: PKCS#7 Signed Message
Digest_Algorithms: MD5
MD5-Digest: (base64 representation of MD5 hash)
MAGIC: UsesMetaData
Integrity-Envelope: PKCS-7
-
-
Manifest-Version: 2.0
Name: http://www.activecontrols.com/shareware/KillerControl.ocx
SectionName: Embedded Signature Object
Digest_Algorithms: MD5
MD5-Digest: (base64 representation of MD5 hash)
MAGIC: UsesMetaData
Integrity-Envelope: Authenticode
The manifest section representing the object with an embedded signature indicates this using the Integrity-Envelope token. The token specifies that the signature was generated by and can be verified by the Authenticode system from Microsoft. No trusted signer is specified because the knowledge of "who" is trusted to have signed the executable is embedded in the specialized signature checker.
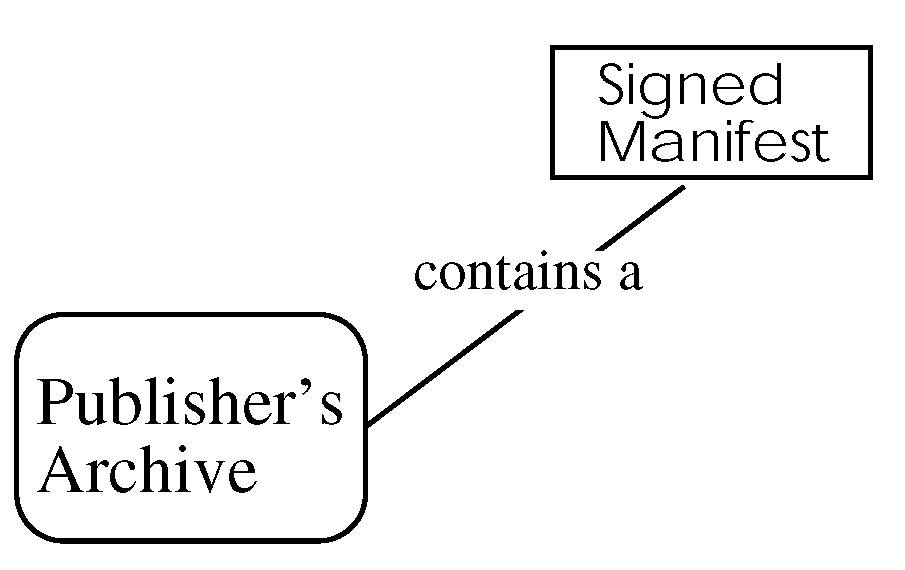
An example manifest for a software publisher's release includes:
-
-
Manifest-Version: 2.0
Name: KillerApp.exe
SectionName: Killer Internet Application
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: KillerApp.hlp
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: KillerApp.doc
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: Readme.txt
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: EULA.txt
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
The signer information description is:
-
-
Signature-Version: 2.0
Name: KillerApp.exe
SectionName: Killer Internet Application
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: KillerApp.hlp
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: KillerApp.doc
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: Readme.txt
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: EULA.txt
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Once the manifest has been created and signed the publisher archives the software release and the signed manifest, and transmits them to a set of distributors.

The distributor creates a new manifest referencing the archive
sent by the publisher:
-
-
Manifest-Version: 2.0
Name: distributor1logo.gif
SectionName: Distributor 1's logo
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: KillerAppArchive
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
The distributor's signature information is:
-
-
Signature-Version: 2.0
Name: distributor1logo.gif
SectionName: Distributor 1's logo
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: KillerAppArchive
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
The distributor creates a new archive, combining the new manifest and the original archive sent by the publisher. This new archive is transmitted to resellers.
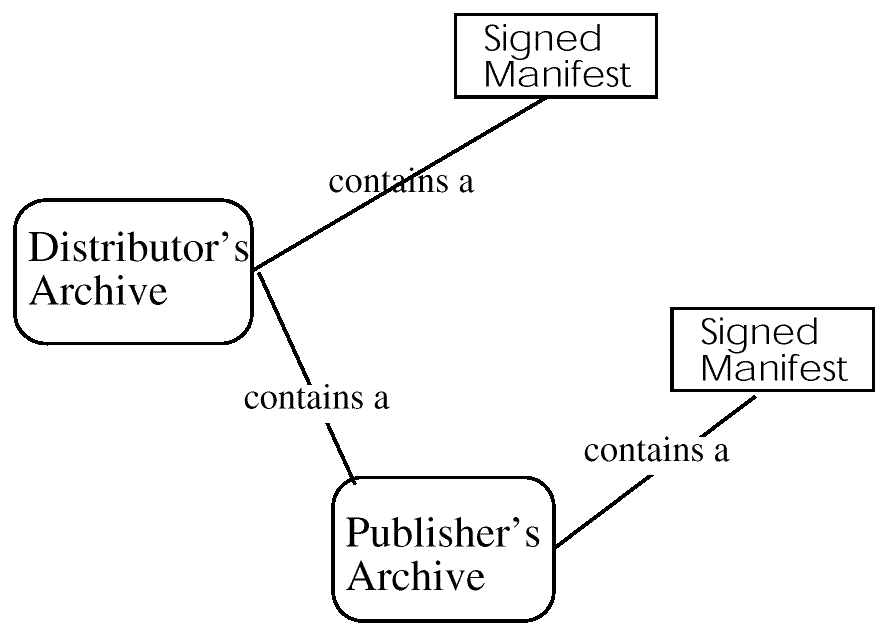
The reseller creates another new archive, adding their own specific
digital objects and including the archive sent by the distributor:
-
-
Manifest-Version: 2.0
Name: reseller1logo.gif
SectionName: Reseller 1's logo
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
Name: distributorarchive
Digest_Algorithms: SHA1
SHA1-Digest: XXXX
The reseller's signature information is:
-
-
Signature-Version: 2.0
Name: reseller1logo.gif
SectionName: Reseller 1's logo
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
Name: distributorarchive
Digest_Algorithms: SHA1
SHA1-Digest: YYYY
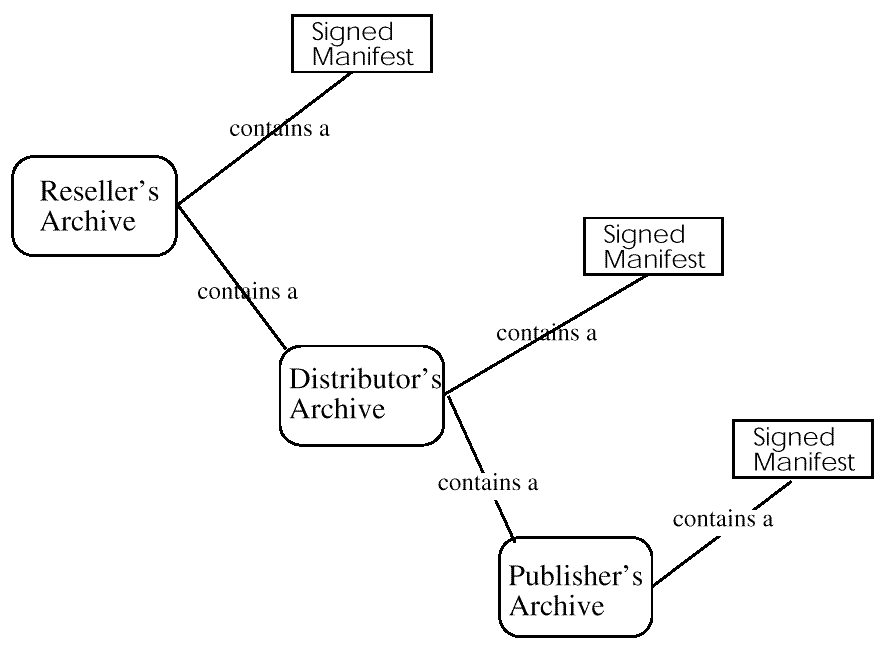
The reseller's archive includes the distributor's archive, which contains the distributor's manifest. The distributor's archive includes the publisher's archive which contains the publisher's manifest. This results in a manifest being implicitly embedded within another manifest which has in it an implicitly embedded manifest. The embedding is implicit because the manifests are referenced indirectly as part of the archive files.
-
-
Manifest-Version: 2.0
Name: http://www.scripts.com/index#script1
SectionName: Useful Javascripts demo home page
Digest_Algorithms: SHA1
SHA1-Digest: xxx
MAGIC: UsesMetaData
Integrity-VerifyData: namedsectionvalue
Integrity-NamedSectionForm: javascript
Only the named section "script1" is used in calculating the signature.
-
-
Manifest-Version: 2.0
Name: http://www.intel.com/developer/ial/security/
Section Name: Intel's Data Security Home Page
Digest_Algorithms: SHA1
SHA1-Digest: xxx
SHA1-Digest: yyy
SHA1-Digest: zzz
MAGIC: UsesMetaData
Integrity-VerifyIntegrity: match
Three hash values are provided, each for a different language representation of the referent object. The integrity token Integrity-VerifyIntegrity specifies that the hash of the referent must match one of the three hash values.
-
-
Manifest-Version: 2.0
Name: telnet://mit.edu/
SectionName: Blessed telnet site
It is not feasible to hash the results of a telnet session. It is useful to list the telnet session as a referent of a manifest because it aggregates the session with other referent objects in the manifest. No hash values are provided for the telnet session because the section hash and hence the referent URL hash are provided in the signature information description.
-
-
Name: MyAudioFile.hqa
Section Name: High Quality Audio File
MAGIC: UsesMetaData
Integrity-ResourceProxy: http://www.HighQualityAudio.com\
/cgi-bin/StreamAudio?SKU=21339191XW
Name: http://www.HighQualityAudio.com/cgi-bin/StreamAudio?\
SKU=21339191XW
Digest_Algorithms: SHA1
SHA1-Digest: xxx
Integrity-ResourceProxy informs the integrity verifier of two facts concerning the referent:
When verifying the referent MyAudioFile.hqa, if the file does not exist in the local directory, then it can be found at: http://www.HighQualityAudio.com/cgi-bin/StreamAudio?SKU=21339191XW
No digest value is indicated in the manifest section for MyAudioFile.hqa. The digest value is specified in the section describing the ResourceProxy.
It is an error to specify a digest value within the same manifest section where Integrity-ResourceProxy has been specified. If encountered the specified digest value will be ignored.
| Contents | Next section | Index |