Previous section.
Authorization (AZN) API
Copyright © 2000 The Open Group
Architectural Overview
The authorization API defined in this Technical Standard
is intended to be used within the architectural framework defined in
ISO 10181-3 - Access Control Framework. This chapter briefly
introduces that framework. Readers are encouraged to consult ISO
10181-3 for more detailed information.
This authorization API defines a programmatic interface through which system
components that need to control access to resources can request an
access control decision
from the system's
access control service.
The ISO 10181-3 access control framework supports access control in both
standalone and networked systems. When this document refers to
the system,
it means "the computer or collection of networked computers
whose resources are protected by the access control service which is
invoked using the authorization API."
ISO 10181-3 Access Control Framework
The ISO 10181-3 Access Control Framework is
illustrated in
ISO 10181-3 Access Control Framework.
The framework defines four roles for
components participating in an access request:
-
Initiators
-
Targets
-
Access Control Enforcement Functions (AEFs)
-
Access Control Decision Functions (ADFs)
Initiators submit access requests. An
access request specifies an operation to be performed on a Target.
Access Control Enforcement Functions (AEFs) mediate access requests.
AEFs submit decision requests to Access Control Decision Functions
(ADFs). A decision request asks whether a particular access request
should be granted or denied.
ADFs decide whether access requests should be granted or denied.
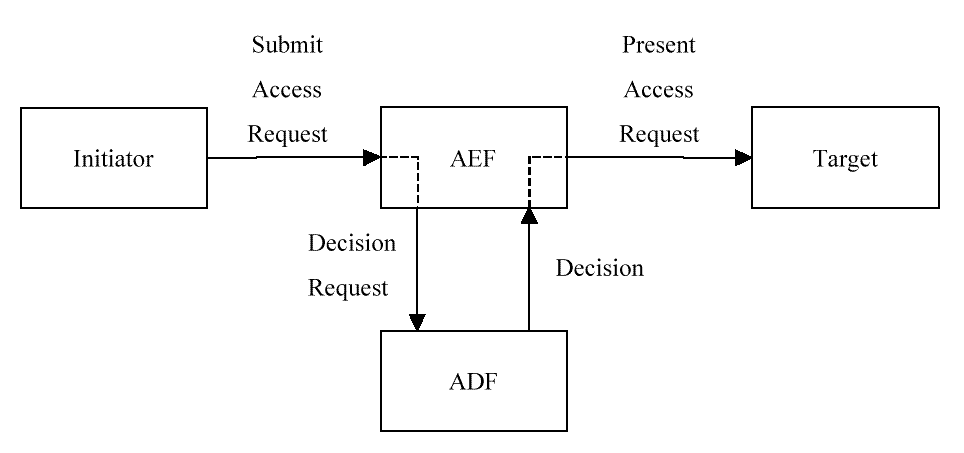
Figure: ISO 10181-3 Access Control Framework
Access Control Service Components
The access control service consists of the
system components assuming the roles of ADFs and AEFs.
Access Control Decision Functions
ADFs make access control decisions based on
Access Control Decision Information (ADI). ADI describes
security-relevant properties of the initiator, the target, the access
request, and the system and its environment. ADI is discussed in
more detail in
Access Control Information.
Inputs to an Access Decision Function (ADF)
shows the information an ADF uses to make an access control decision.

Figure: Inputs to an Access Decision Function (ADF)
Access Control Enforcement Functions
Access Control Enforcement Functions
enforce access control decisions made by ADFs.
The authorization API
(referred to hereafter as aznAPI) is the medium through which AEFs call
on ADFs to obtain access control decisions. AEFs use the aznAPI to
present Access Control Information (ACI) to ADFs. As
AEFs Use the Authorization API to Call ADFs
illustrates, the implementation of the aznAPI is responsible for
deriving ADI from the ACI provided by an AEF and presenting the ADI to
an ADF. The ADF then uses this ADI, together with access control
policy rules and with context ADI it derives from its environment, to
make an access decision.
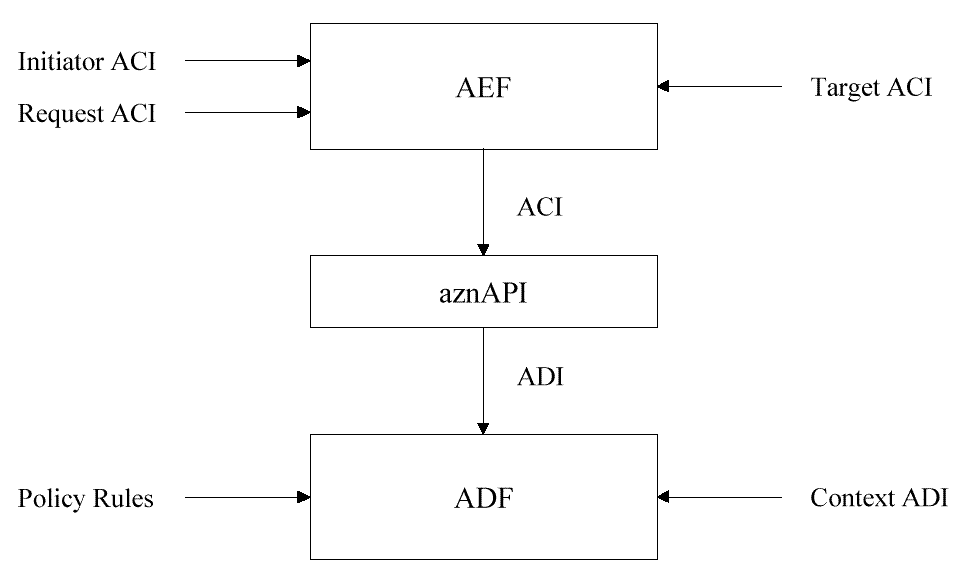
Figure: AEFs Use the Authorization API to Call ADFs
Access Control Information
Access Control Information, or ACI, is the set of
all the information available to an AEF which might be relevant to an
access control decision. The aznAPI is responsible for:
-
Determining which of the ACI presented by the AEF is relevant to the
access control decision the AEF requested
-
Transforming the ACI
presented by the AEF into ADI in a form which can be used by the ADF
-
Presenting the resulting ADI to the ADF
There are several kinds
of Access Control Information.
The main kinds describe authorization-relevant properties
of the initiator, the target, the access request,
and the context within which the request was made.
Initiator Information
Initiator information describes security-relevant
properties of the initiator of an access request:
-
Initiator ACI is the initiator information which is available to AEFs.
-
Initiator ADI is the initiator information which results from
the aznAPI's transformation of initiator ACI and is made available to ADFs.
Initiator ACI
An initiator ACI data structure which is produced by an authentication
service is called (in this specification) an
identity.
Identities may
be as simple as a string containing the initiator's name, or they may
be as complex as an X.509 digital certificate.
The aznAPI may also accept a
capability
as an Identity. A capability is a direct
assertion by an authentication service of the capability holder's
authorization to perform specific operations on specific targets. As
A Capability
shows, a capability is asserted (using a
signature, for example) by some authority. A capability does not
necessarily name its initiator; whoever possesses a capability can use
it. In
A Capability,
this is indicated by the dotted line around the
initiator identity. Finally, a capability contains a list of policy
entries. Each entry names a target object and defines a rule which
describes the operations which it allows the initiator to perform.
Note that aznAPI implementations are not required to support any
particular identity format, and are specifically not required to
support capabilities.
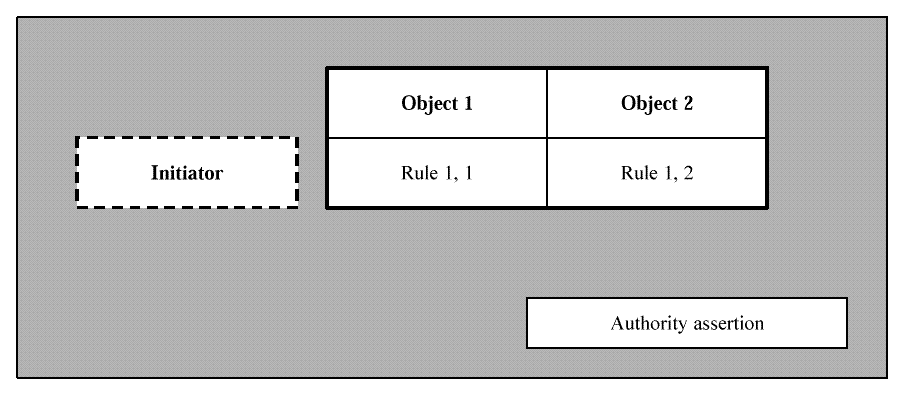
Figure: A Capability
An initiator ACI data structure which is
produced by an authorization service (using the aznAPI's credential
externalization function) is called a PAC. Note that authorization
services are not the only things which can create PACs. Authentication
services also create PACs to assert users' identities. In
push-model environments, they are the user's privilege attributes. (aznAPI
implementations treat PACs created by authentication services as
Identities
in order to distinguish them from the authorization data
structures they create themselves.) aznAPI implementations might even
use PAC data structures to contain their internal representations of
user credential information, but these data structures are not
exposed to AEFs through the aznAPI. PACs are discussed in more detail
in
Externalizing ADI.
Initiator ADI
Initiator ADI is the authorization-relevant data which is
derived from Initiator ACI, and passed to ADFs by the aznAPI.
Initiator ADI is stored by the aznAPI in structures called "credentials"
chains. Since credentials chains are never passed to callers of the
aznAPI, and since different authorization services may use different
credentials chain formats, the format of credentials chain data
structures is not defined or constrained by the aznAPI specification.
Although the aznAPI does not allow callers to access credentials chains
directly, it does provide functions through which attribute information
may be retrieved from credentials chains.
Transforming Initiator ACI into a Credential
shows
how the aznAPI transforms Initiator ACI into credentials chains, and
returns a
credential handle
to the caller. Note that the aznAPI can
be used in systems which "push" privilege attributes from clients to
AEFs, or in systems which require AEFs to "pull" privilege attributes
from a repository or service. In push-model environments, the
Initiator ACI will contain the privilege attributes pushed by the
client, and will be translated into an internally usable form by the
aznAPI implementation. In pull-model environments, the Initiator ACI
typically contains only a single privilege attribute (for example,
the authenticated name of the Initiator), and the aznAPI implementation
pulls the rest of the Initiator's privilege attributes from the
appropriate repository or structure during construction of the
Initiator's credentials chain.
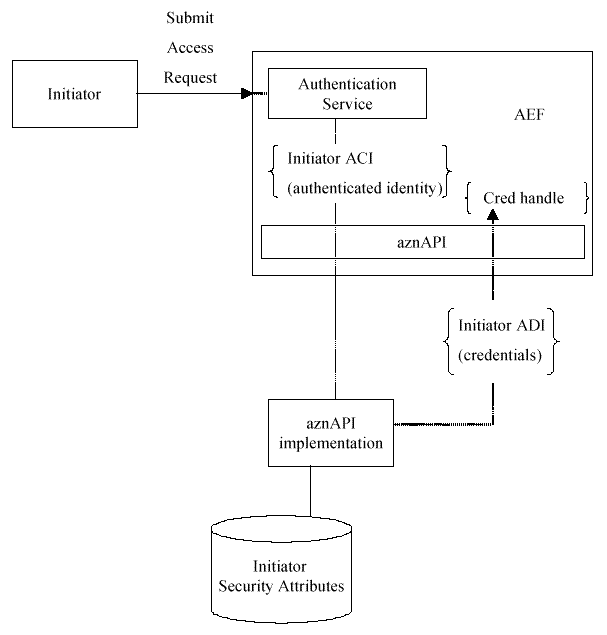
Figure: Transforming Initiator ACI into a Credential
Target Information
Target information describes security-relevant properties
of the target of an access request:
-
Target ACI is the target information which is available to AEFs.
-
Target ADI is the target information which results from the
aznAPI's transformation of target ACI.
Target ACI
Normally the only ACI data which the aznAPI requires is the
name
of the target.
Labels are an exception to this rule. The
aznAPI has been designed to support access control decisions based on
ADI contained in security labels. In some label-based authorization
systems, however, the authorization service may not know how label
information is encoded into the target, or how it is stored as metadata
associated with the target. In these cases, the AEF needs to
retrieve the target's
labels
and pass them to the aznAPI as target
ACI. The aznAPI also supports implementations which can handle several
different types of labels. Implementations which support multiple
label types may require their callers to specify a labeling scheme ID
identifying which type of label is being used in a particular call.
Target ADI
Different authorization service implementations may have
very different types and amounts of target ADI data. Target ADI data
is generally not returned to callers of the aznAPI, so the format of
target ADI data is not defined or constrained by the aznAPI
specification.
Some callers of the aznAPI may want to use
authorization policy data for purposes other than making access control
decisions. For this reason, the aznAPI supports externalization of ADI
data into data structures called
entitlements.
Entitlements are
discussed in more detail in
Externalizing ADI.
Request Information
Request information describes security-relevant properties of an access
request:
-
Request ACI is the request information which is available to AEFs.
-
Request ADI is the request information which results from the
aznAPI's transformation of request ACI.
Request ACI
The only ACI data
which the aznAPI requires is the name of the
operation
which was requested.
Request ADI
Different authorization service implementations
may have very different types and amounts of request ADI data. Request
ADI data is not returned to callers of the aznAPI, so the format of
request ADI data is not defined or constrained by the aznAPI
specification.
Context Information
Context information describes
security-relevant properties of the context in which an access request
occurs. Context ACI is the context information which is available to
AEFs.
There are two sources of context ADI:
-
The first source is the
context information which results from the aznAPI's transformation of
context ACI.
-
The second source is context information which was not
provided as ACI but which is directly accessible to the authorization
service.
Context ACI
The aznAPI defines four Context ACI data types
which can be used to pass context information to authorization
services:
-
Time:
The time at which the request occurred.
-
Location:
The location (source address) from which the request was initiated.
-
Route:
The security characteristics of the connection over which the request
was transmitted from the initiator to the AEF.
-
Quality of Authentication:
The quality of authentication used to establish the
initiator's identity.
In addition, the aznAPI allows AEFs to pass
application-specific or authorization-service-specific
context information, not
limited to the above types, to authorization services using an
opaquely-typed parameter. Use of this functionality will result in
applications which cannot portably use authorization services which do
not support the particular context information format passed through
the opaque parameter.
Context ADI
Different authorization service
implementations may have very different types and amounts of context
ADI data. Context ADI data is not returned to callers of the aznAPI,
so the format of context ADI data is not defined or constrained by the
aznAPI specification.
Retained Information
The authorization
service may retain information to make access control decisions about
sequences of operations requested by the same initiator. For example,
an authorization service used by a bank's Automated Teller Machine
(ATM) network might retain information about how much money each user
has withdrawn during the day in order to enforce a daily withdrawal
limit policy.
Information retained by the authorization service for
this purpose is ADI, and is never exposed to applications by the
aznAPI. Therefore, the format of retained ADI is not defined or
constrained by the aznAPI specification (retained ADI might in some
circumstances be of interest to applications, but exposing retained ADI
is not supported by this version of aznAPI).
Access Control Policy Information
Access Control Policy Information consists of the
rules which the ADF uses to evaluate the other types of ADI and make an
access control decision. The aznAPI does not normally make access
control policy information available to callers, and different
authorization services may use very different types and amounts of
access control policy information, so the format of access control
policy information is not defined or constrained by the aznAPI
specification. Authorization services can, however, externalize access
control policy information in the form of entitlements, as described in
Externalizing ADI.
Externalizing ADI
The aznAPI deliberately
hides the details of initiator ADI and access control policy
information from its callers. However, this information can be useful
to callers under some circumstances. Therefore, the aznAPI allows
authorization services to
externalize
initiator ADI and access control
policy information.
PACs
The aznAPI puts externalized initiator ADI
into a structure called a PAC.
Externalization of Credentials into a PAC
illustrates the creation of a PAC.
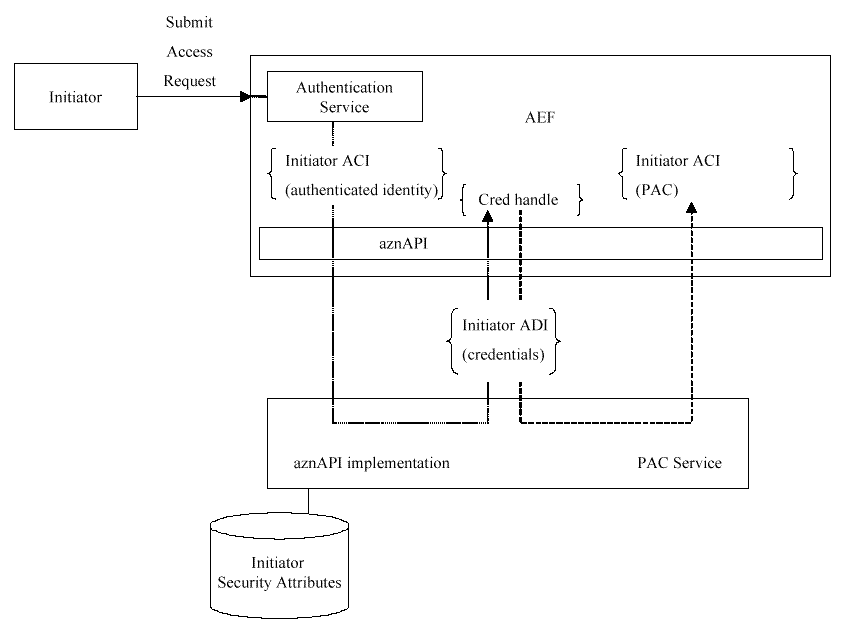
Figure: Externalization of Credentials into a PAC
Externalization of
initiator ADI allows the authorization service to assert its view of
the security-relevant characteristics of the initiator, as distinct
from the authentication service's view of the same initiator's
security-relevant characteristics.
An authorization service could (but
is not required to) use this functionality to generate
signed
attribute certificates which other services could rely on as sources of
authorization data.
Because this specification defines only an opaque
PAC structure, PACs produced by one authorization service are not
guaranteed to be usable by another authorization service. However, a
standard PAC structure could be defined in a future specification as
the basis for interoperable assertion of initiators' authorization
attributes by authorization services.
- Note:
- It is important to note that
Signed PACs
can be used as building blocks when constructing delegation protocols. The
aznAPI does not, however, provide a delegation service. A delegation
protocol must allow entities which wish to become delegates for
requests received from an initiator to pass the following to a target:
-
The delegated request
-
A trustworthy indication that the
request originally received from the initiator was authenticated
-
A trustworthy representation that the delegate is authorized to
forward the request to the target on the initiator's behalf
-
A trustworthy representation of the initiator's and the delegate's
credential information
Although the authorization service may sign PACs
to form trustworthy representations of initiators' and delegates'
credential information, and may even include identity information (such
as a certificate issuer identity and identity certificate serial
number) in a signed PAC to establish a link to the authentication data
of the initiator, it does
not
bind PACs to requests (cryptographically or in any other way). AEFs which wish to impersonate or otherwise serve
as delegates for initiators must use a separate cryptographic facility
or delegation service to bind the PACs generated using the aznAPI to
delegated request messages.
- Note:
- The term
delegation
is used here
in the sense in which the DCE and SESAME systems use the term.
Delegation
is thus the security function through which an
intermediary issues a request for access to a protected resource on
behalf of an initiator from which it has itself received an access
request. Other documents, notably X.509, use the term
delegation
with a different sense.
Entitlements
The aznAPI puts externalized access
control policy information into structures called
entitlements.
Externalization of access control policy information allows
applications to customize the behavior of the system based on
authorization policy. For example, it allows applications to modify
system menus to display only operations which an initiator is permitted
to access, rather than displaying all system operations and responding
to the initiator's attempts to perform prohibited operations with an
access denied
message. Entitlement information could also be used by
applications which want to make their own access decisions rather than
relying on the ADF implemented by the authorization service.
The aznAPI defines a portable format for entitlement data that every
authorization service can support - a list of the operations a
particular initiator may (or may not) perform on a particular target.
Portable Entitlements
shows this format. Note that the dotted line
around the subject data indicates that the initiator information is
implicit; it is not returned by the aznAPI as part of the entitlement
data.

Figure: Portable Entitlements
The portable entitlement data
representation is guaranteed to be supportable by all authorization
service implementations, but it is not very efficient. Some
authorization services may be able to express an initiator's
authorizations to many operations on many targets using a single rule,
or using a wildcarded expression. They may even be able to describe
many initiators' authorizations in a single rule or expression.
However, different authorization services use different rule formats,
and there is no single rule format which can express all authorization
services' rules efficiently. For this reason, the aznAPI allows
authorization services to return non-portable entitlement information
through an opaquely-typed parameter. As
Non-Portable Entitlements
illustrates, non-portable entitlement data may be in any rule format.
Figure: Non-Portable Entitlements
Use of non-portable entitlements
requires the application calling the aznAPI to understand the
authorization service's rule format, and prevents the application
calling the aznAPI from using other authorization services with
different rule formats.
Why not acquire a nicely bound hard copy?
Click here to return to the publication details or order a copy
of this publication.








