Bonus Section D: Technology Architecture
JJ starts by giving some background on where the ArchiSurance buildings are located and some of the connectivity requirements. He then goes into the details of the Technology Architecture.
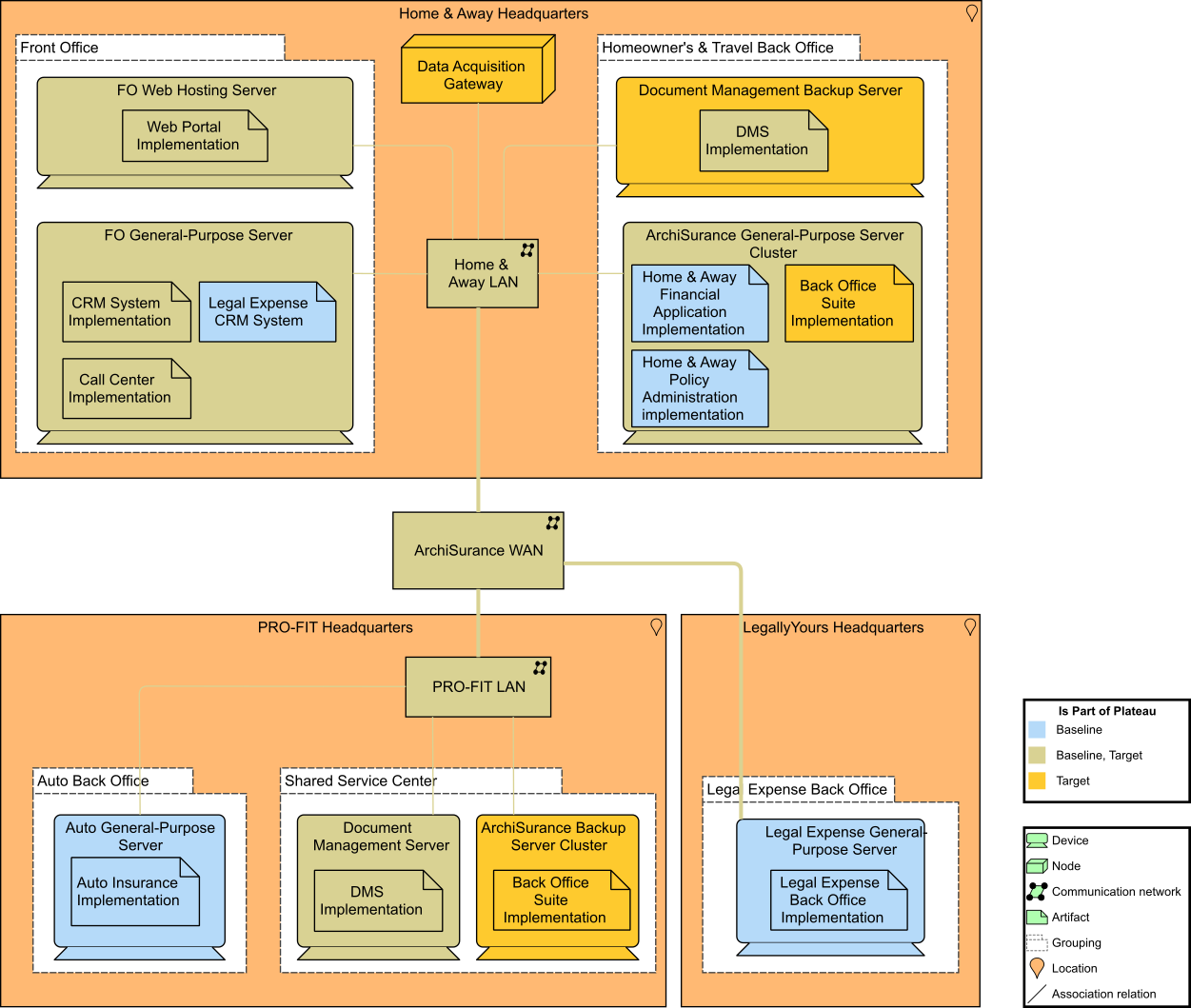
First, he reminds everyone, in the ArchiSurance front office, located at the Home & Away headquarters, that there is a general-purpose server and one dedicated to web hosting. The Shared Service Centre (SSC), located at the PRO-FIT headquarters, has its own server for the document management system. Each of the three back offices has a server for its applications.
A Local Area Network (LAN) connects servers and personal computers at each of the three ArchiSurance locations, which are in turn connected by a corporate Wide Area Network (WAN). The infrastructure viewpoint contains the software and hardware infrastructure elements supporting the Application Layer, such as physical devices, networks, or system software, such as operating systems, databases, and middleware.
JJ has created an infrastructure view (Infrastructure View (Baseline)) that shows the main infrastructure components of ArchiSurance, grouped by location and department. Also shown in this view are the networks that connect the different devices, and the (application) artifacts deployed on them.
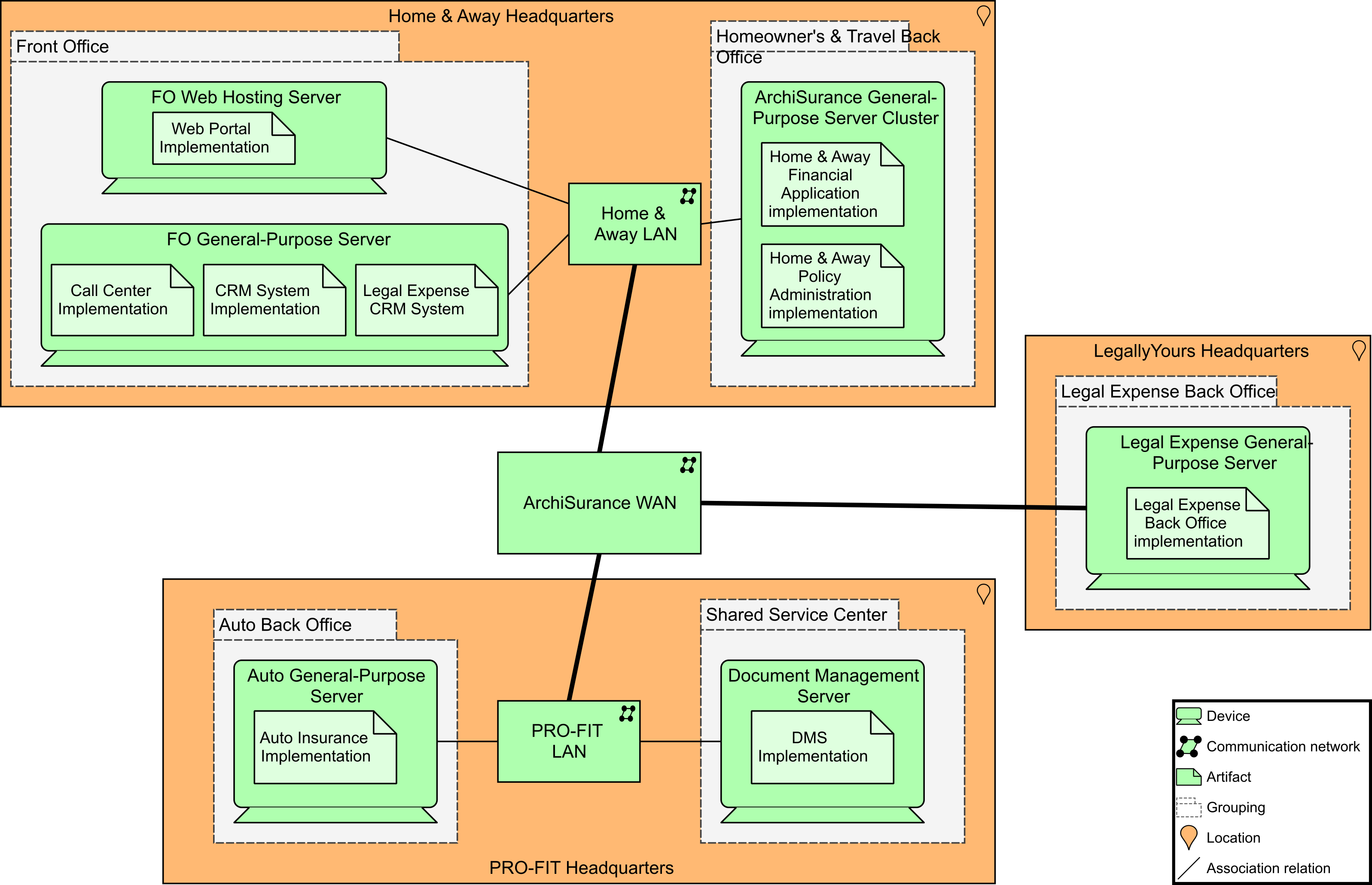
From there, JJ created the Target View (Technology Architecture: Infrastructure View (Target)) to show the proposed technical infrastructure landscape. This is the type of information needed to keep in front of the developers as they are building their MVPs. JJ is very much in agreement with CK that there is a need to work more closely with the DevOps team to give them the information they need to make informed decisions about their builds.
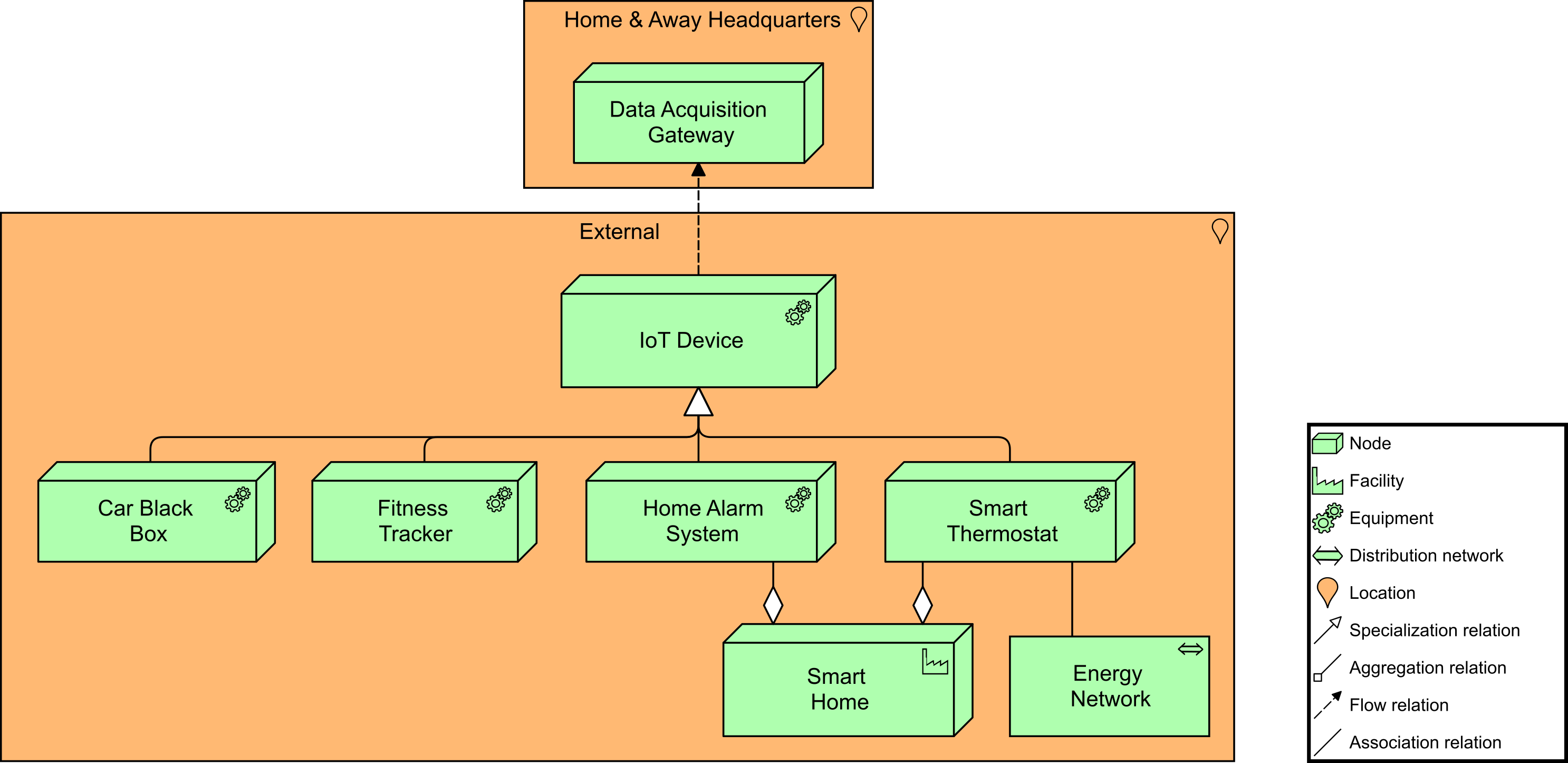
JJ continues by saying that in a separate set of views, the IoT-based data acquisition (Data Acquisition from IoT Services (Target)) was also visualized as outlined in its new Digital Customer Intimacy strategy. To support this, a data acquisition gateway will be established that can connect to all kinds of smart devices which generate relevant data. These devices are modeled as equipment. In turn, equipment can be located at a facility. For example, in this detail of the Target Data Acquisition from IoT Services you can see a “Home Alarm System” and “Smart Thermostat” within a “Smart Home”. Finally, the smart thermostat itself is connected to the “Energy Network”, modeled as a distribution network in the ArchiMate language.
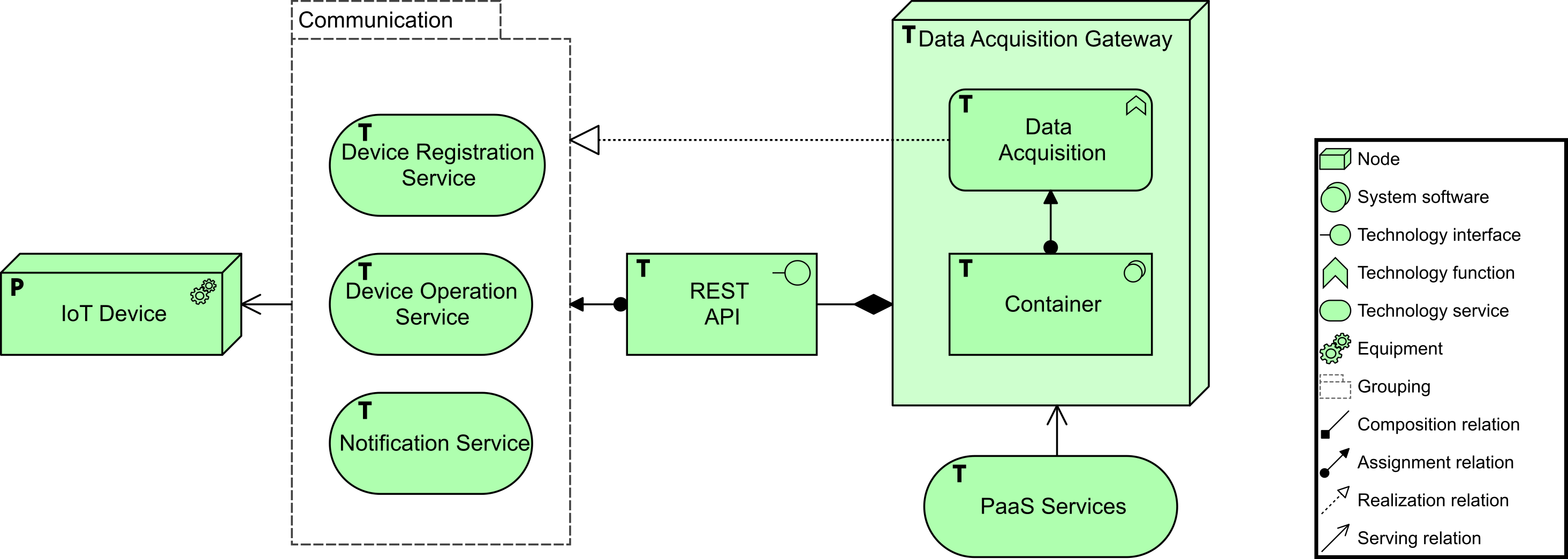
JJ continues, saying that the implementation of ArchiSurance data acquisition is based on a microservices architecture. IoT devices can register themselves with the gateway via a REST3 API. It also uses services on the API to notify the gateway of the data it acquires. For each registered device, an instance of the data acquisition functionality will run in a container. The gateway itself is supported by a Platform as a Service (PaaS), providing services for deployment, integration, service lifecycle management, accounting, security, load balancing, storage, virtualization, and more, as shown in our depiction of the target for IoT device services (IoT Device Services (Target)).
D.1 Technology Gap Analysis
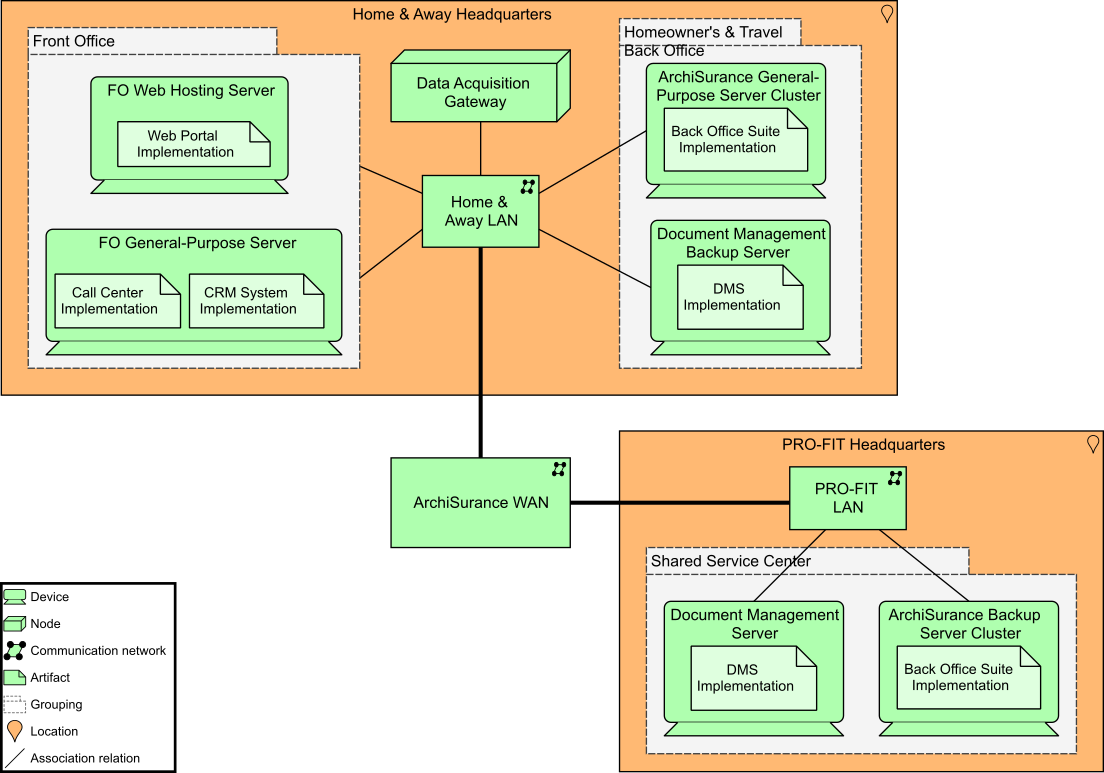
Next, we created a visualization of the results of a global gap analysis we ran for the Technology Architecture (Technology Architecture: Gap Analysis). The separate general-purpose back office servers are slated for removal. The original server cluster of Home & Away is to become the central ArchiSurance back office service cluster, and an additional backup server cluster is to be placed in the SSC at PRO-FIT headquarters. A backup document management server is also to be placed in the Home & Away back office. The new back office suite and the document management system are to be replicated on their respective main servers and backup servers.
JJ asks if there are any questions about the Technology Architecture.
GM asks about information security and the cybersecurity implications for IoT.
JJ replies that cybersecurity is taken very seriously. He has also been working on the security plan, with a whole section on IoT device compliance. A key requirement is the ability to track these smart devices on the network, and to know where they are in case of a cyberattack that would require them to be removed from our environment. Since last year, supplier contracts demand that they must notify us if a product has a cybersecurity issue. We are considering the purchase of software that gives the latest updates on cybersecurity issues with IoT devices. JJ asks if there are any other questions.
KS tells both CK and JJ she is very impressed with their work.