1. Digital Value
1.1. Introduction
As noted at the outset, you are a small core of a startup. Your motivations are entrepreneurial; you want to create a successful business. You might be housed within a larger enterprise, but the thought experiment here is that you have substantial autonomy to order your efforts. You want to do something that has a unique digital component. Regardless of your business, you will need accounting and legal services at a minimum and, very quickly, payroll, HR, and so forth. Those things can (and should) be purchased as commodity services if you are a small entrepreneur (unless you are absolutely on the smallest of shoestring budgets and can work 100-hour weeks). Your unique value proposition will be expressed to some degree in unique IT software. While this software may be based on well-understood products, the configuration and logic you construct will be all your own. Because of this, you are now a producer (or soon to be) of IT services.
Before we can talk about building and managing IT-based (aka digital) products, we need to understand what IT is and why people want it. We’ll start this chapter by looking at an IT value experience that may seem very familiar. Then we’ll dig further into concepts like the IT stack and the IT service and how they change over time.
1.1.1. Chapter outline
-
An IT value experience
-
What is IT?
-
The IT service and the IT stack
-
The IT service
-
IT changing over time
-
The digital context
-
Conclusion
1.1.2. Learning objectives for this chapter
-
Explain “IT value” in everyday terms
-
Distinguish between IT service and IT system
-
Discuss how IT services change over time
-
Describe various ways of understanding the context in which digital systems are developed and digital value is delivered
1.2. What is digital value?
1.2.1. A digital value scenario

Consider the following scenario:
A woman (Dinner out tonight? [1]) is wondering if she can afford to dine out that evening. She uses her mobile device to access her banking information and determines that in fact she does have enough money to do so. She also uses her mobile device to make a reservation and contact some friends to join her. Finally, she uses social navigation software to avoid heavy traffic, arriving at the restaurant in time for an enjoyable evening with her friends.
IT pervaded this experience. The origins, layers, and complex connections of the distributed systems involved are awe-inspiring to consider.
|
Important
|
Don’t worry about the technological terms for now. This is an introductory text. You may see terms below that are unfamiliar (model-view-controller, IP, packet switching). If you are reading this online, you can follow the links, but it’s not required. As you progress in your career, you will always be encountering new terminology. Part of what you need to learn is when it’s important to dig into it and when you can let it pass for a time. You should be able to understand the gist presented below that these are complex systems based on a wide variety of technologies, some of them old, some new. |
The screen on her cell phone represents information accessed and presented by a complex "architecture" of distributed systems, including her cell phone’s hardware and operating system, which run software written and deployed by the bank, which communicates with computers ("servers") in the bank’s data center. The communication with her bank’s central systems is supported by 4G LTE data which in turn relies on the high-volume IP backbone networks operated by the telecommunications carriers, based on research into packet switching now approaching 50 years old. The application operating on the cell phone interacts with core banking systems via sophisticated and highly secure middleware, crossing multiple network control points. This middleware talks in turn to the customer demand deposit system that still runs on the mainframe.
The mainframe is now running the latest version of IBM’s z/OS operating system (a direct descendant of OS/360, one of the most significant operating systems in the history of computing). The customer demand deposit banking application running on the mainframe is still based on code written in the lowest level assembler. Some of the comments in this code date back to the 1970s. It has been tuned and optimized over the decades into a system of remarkable speed and efficiency. Although re-platforming it is periodically discussed, the cost/benefit ratio for such a project has to date not been favorable.

The reservation system looks similar on the mobile device, but the network routes it to a large cloud data center hosting the reservation system. The back-end application here is very different from the banking system; the programming languages are newer, the database is structured very differently, and the operating system is Linux.
Finally, the navigation software looks much like the reservation system, as it too is based on the cloud. However, the system is much more active as it is continually processing inputs from millions of drivers in thousands of cities and updating traffic maps for those drivers in real time so that they can choose the most optimal route to their destinations (e.g., dinner). The capabilities of this system are comparable to an air traffic control system, and yet it is available as a free download for our IT user.
The resulting value (as in Digital made this gathering easier [2]) is clear:
-
In an earlier era, our user might have stayed in for fear of bouncing a check, or she might have gone out and dined beyond her means.
-
The phone line at the restaurant might have been busy, so she might have risked showing up with no reservation.
-
Before texting and social media, she might not have been able to reach her friends as easily.
-
Without the traffic application, she might have run into a huge midtown traffic jam and been half an hour late.
Clearly, IT added value to her life and helped maximize her experience of social enjoyment.
1.2.2. Various forms of digital value
As we have seen, there are many ways in which digital systems deliver value. Some systems serve as the modern equivalent of file cabinets: massive and secure storage for financial transactions, insurance records, medical records, and the like. Other systems enable the transmission of information around the globe, whether as emails, web pages, voice calls, video on-demand, or data to be displayed in a smartphone application (app). Some of these systems support engaged online communities and social interactions with conversations, media sharing, and even massive online gaming ecosystems. Yet other systems enable penetrating analysis and insight by examining the volumes of data contained in the first two kinds of systems for patterns and trends. Sophisticated statistical techniques and cutting-edge approaches like neural network-based machine learning increase the insights our digital systems are capable of, at a seemingly exponential rate.
Digital technology generates value in both direct and indirect ways. People have long consumed (and paid for) communication services, such as telephone services. Broadcast entertainment was a different proposition, however. The consumer (the person with the radio or television) was not the customer (the person paying for the programming to go out over the airwaves). New business models sprung up to support the new media through the sale of advertising air time. In other words, the value proposition was indirect, or at least took multiple parties to achieve: the listener, the broadcaster, and the advertiser. Finally, some of the best known uses of digital technology were and are very indirect -— for example, banks and insurance agencies using the earliest computers to automate the work of thousands of typists and file clerks.
From these early business models have evolved and blossomed myriads of creative applications of digital technology for the benefit of human beings in their ongoing pursuit of happiness and security. We see the applications mentioned at the outset: online banking, messaging, restaurant reservations, and traffic systems. Beyond that we see the use of digital technology in nearly every aspect of life.
Digital and IT pervades all of the major industry verticals (e.g., manufacturing, agriculture, finance, retail, healthcare, transportation, services) and common industry functions (e.g., supply chain, human resources, corporate finance, and even IT itself). Digital systems and technologies also are critical components of larger-scale industrial, military, and aerospace systems. For better or worse, general-purpose computers are increasingly found controlling safety-critical infrastructure and serving as an intermediating layer between human actions and machine response. Robotic systems are based on software, and the Internet of Things ultimately will span billions of sensors and controllers in interconnected webs monitoring and adjusting all forms of complex operations across the planet.
1.3. Defining digital
In order to define digital, let’s start with discussing Information Technology, commonly abbreviated "IT."
1.3.1. What is IT, anyways?
We’ve started this book in the previous section by providing an example of digital or IT value, without much discussion of how it is delivered. This is deliberate. But what is IT, anyways?
-
The computers? The networks?
-
The people who run them?
-
That organization under a Chief Information Officer that loves to say “no” and is always slow and expensive?
None of these are how this book defines “IT.” Although this is not a technical book on computer science or software engineering, the intent is that it reflects and is compatible with foundational principles.
“Information Technology” is ultimately based on the work of Claude Shannon, Alan Turing, Alonzo Church, John von Neumann, and the other pioneers who defined the central problems of information theory, digital logic, computability, and computer architecture.
Additionally, as an organizational function, IT also draws on organizational theory, systems theory, human factors and psychology, and more recent concepts such as design thinking, among many other areas. Discussions of “IT” become contentious because some think of the traditional organization, while others think of the general problem area. IT has a long history as a corporate function, a single hierarchy under a powerful Chief Information Officer. This model has had its dysfunctions, including a reputation for being slow and expensive. Often, when one encounters the term “IT,” the author using the term is referring to this organizational tradition.
We are less interested in the future of IT as a distinct organizational structure. There are many different models, from fully centralized to fully embedded. Organizational structure will be discussed in Part III.
For this book, we define “Information Technology” in terms of its historic origins. We look to IT’s common origins in automating the laborious and error-prone processes of computation, through the application of digital logic technologies based on information transmission.
Regardless of organizational form or delivery methods, IT is defined by these origins. It does not matter if the application developers and systems engineers ultimately report up through the CIO, the CMO, the CFO, or the COO. There are common themes throughout IT and digital as a professional domain: the fragility and complexity of these systems, the need for layered abstractions in their management, and more.
1.3.2. IT and digital transformation
IT doesn’t matter. [54]
Software is eating the world. [15]
The digital realm is infusing the physical realm, like tea in hot water. [261]
Designing Delivery
IT increasingly permeates business operations and social interactions. The breadth and depth of IT support for virtually all domains of society continues to expand. Lately, this is known as Digital Transformation [281].
The role of IT seems critical to society and the economy, but there are various points of view. Nicholas Carr, in his controversial Harvard Business Review article “IT Doesn’t Matter,” recognized that IT was becoming commoditized in an important sense [54]. As cloud providers started to offer utility-style computing, the choice of particular vendors of computers was no longer strategic. Looking to history, Carr argued that just as businesses no longer have “Vice Presidents for Electricity,” so businesses no longer need Chief Information Officers or dedicated IT departments.
|
Note
|
A “commodity” product is one that is offered from a variety of suppliers, with little or no difference between their offerings. Commodity products tend to compete on price, not on differences in features. Wheat is a commodity. Sports cars are not. “Commoditization” is the process by which products that used to compete by being different, increasingly compete on price. |
Carr has insight -— there is no question IT is becoming pervasive -— but he ultimately reflects a narrow view of what “IT” is. If “IT” were merely computation at the lowest level -— just shuffling bits of information around, doing a little math -— then perhaps it could be embedded throughout a business like electricity.
But IT has emergent aspects that are not comparable to electrical power. As it pervades all dimensions of business operations, it brings its concerns with it: complexity, fragility, and the skills required to cope with them.
One watt of electrical power is like any other watt of electrical power, and is therefore a commodity. We can use it to run toasters, hair dryers, or industrial paint mixers, and there is little concern (beyond supply and demand management) that the consumption of power by the paint mixer will affect the toaster. It’s also true that one cycle of computing, in a certain sense, is like any other cycle. But IT systems interact with each other in surprising and unpredictable ways, orders of magnitude more complex than electrical power grids. (This is not to imply the modern electrical grid is a simple system!)
IT also radically transforms industries: from retail to transportation to manufacturing to genetics. Applied software-centric IT is unleashing remarkable economic disruption.
A lawyer may depend on a cell phone, but (in keeping with Carr) beyond its provision as a commodity service, it’s not a differentiator in delivering the legal strategies a firm needs. A graphic designer may use computerized graphic tools, but these have become relatively standardized and commoditized in the past 20 years, and probably are not a source of competitive advantage in the quest for new marketing clients.
On the other hand, consider a text analytic algorithm that replaces thousands of paralegals, resulting in order-of-magnitude more accurate legal research in a fraction of cost and time. This is strategic and disruptive to the legal community. A superior supply chain algorithm, and the ability to improve it on an ongoing basis, may indeed elevate a logistics firm’s performance above competitors. In cases like these -— and they seem to be increasing -— IT matters very much. The annual State of DevOps research finds that “Firms with high-performing IT organizations were twice as likely to exceed their profitability, market share, and productivity goals.” [95]
In the digitally transforming economy, traditional “back office” IT organizations find themselves called on to envision, develop, and support market-facing applications of IT. And what starts with one market-facing use case can quickly expand into entire portfolios. It is such cases that are of particular concern in this book. Ultimately, it is possible that IT is the most strategic capability an organization can invest in. As Diomidis Spinellis, editor in chief of IEEE Software notes [256],
“…other industries are also producing what’s in effect software (executable knowledge) but not treating it as such … Although many industries have developed their own highly effective processes over the years, software engineering maintains an essential advantage. It has developed methods and tools that let even small teams manage extremely high complexity … This advantage is important because the complexity in non-software activities is also increasing inexorably … the time has come to transform our world … by giving back to science and technology the knowledge software engineering has produced.”
This ability to manage complexity, to turn tacit into explicit and formalize the previously unstructured, is an essential aspect of Digital Transformation.
1.3.3. Defining “IT”
So, how do we define an IT problem, as opposed to other kinds of business problems? An IT problem is any problem where you are primarily constrained by your capability for and understanding of IT.
-
If you need computer scientists or engineers who understand the fundamentals of information theory and computer science, you are doing IT.
-
If you need people who understand when your information-centric problems might need to be referred to such theorists and engineers, you are likely doing IT.
-
If you need people who are skilled in building upon those fundamentals, and operating technical platforms derived from them (such as programming languages, general-purpose computers, and network routers), you are doing IT.
Regardless of whether IT is housed under a traditional CIO, an operations capability, a Chief Marketing Officer (CMO), or a “line of business”, when it is critical to operations certain concerns inevitably follow:
-
Requirements (i.e., your intent for IT)
-
Sourcing and provisioning
-
IT-centric product design and construction
-
Configuration and change management
-
Support and operations
-
Security
-
Improvement
Newcomers who propose changes to these practices in hopes of making IT more “Agile” are often surprised to find that these concerns were not mere bureaucracy, but instead had well-grounded origins in past failures. Ignoring these lessons is perilous. And yet, the traditional, process-heavy IT organization does seem dysfunctional from a business point of view: a central theme of this book.
1.3.4. IT versus "Digital"
So, is there any real difference between "IT" and "Digital"? Perception is important, and IT as a term is becoming outdated. It is associated with an earlier generation of centralized computers running back-office systems. "Digital," on the other hand, is associated with the everyday experience of computers and software, pervasive throughout our lives. "Digital" of course is based on IT, if we are to be precise in our use of words. But the social and marketing connotations are clearly distinct.
This book is not completely precise in distinguishing the two terms, and this is to some extent deliberate. But in general, if you think of "IT" as more structured and internal, and "digital" as more market-facing, you will be on the right track.
1.4. Digital services, systems, and applications
1.4.1. Inside a digital service
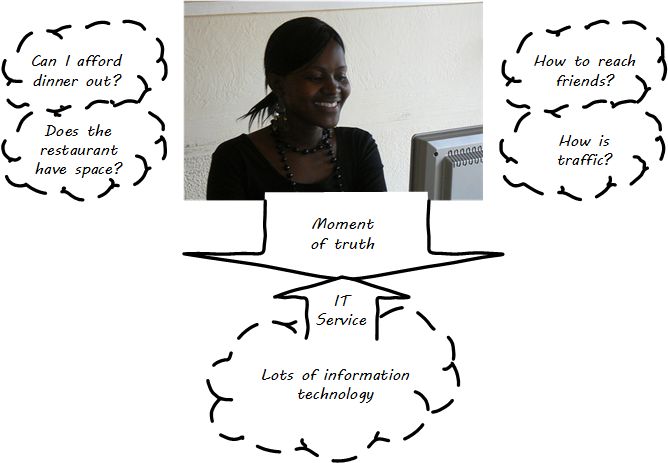
Let’s examine our diner’s value experience (The basis of digital value [3]) in more detail, without getting unnecessarily technical, and clarify some definitions along the way. The first idea we need to cover is the "moment of truth.” In terms of IT, this English-language cliche (elaborated into an important service concept by SAS group president Jan Carlzon [53]) represents the user’s experience of value.
In the example, our friend seeking a relaxing night out had several moments of truth:
-
Consulting her bank balance, and subsequent financial transactions also reflecting what was stated to her
-
Making a reservation and having it honored on arrival at the restaurant
-
Arriving on time to the restaurant, courtesy of the traffic application
-
And most importantly, having a relaxed and refreshing time with her friends
Each of these individual value experiences was co-created by our friend’s desire for value, and the response of a set of IT resources.
|
Important
|
The “moment of truth” represents the user’s experience of value from a product. |
In order to view her balance, our user is probably using an application downloaded from a “store” of applications made available to her device . On her device, this “app” is part of an intricate set of components performing functions such as:
-
Accepting “input” (user intent) through a screen or voice input
-
Processing that input through software and acting on her desire to see her bank balance
-
Connecting to the phone network
-
Securely connecting over the mobile carrier network to the Internet and then to the bank
-
Identifying the user to the bank’s systems
-
Requesting the necessary information (in this case, an account balance)
-
Receiving that information and converting it to a form that can be represented on a screeen
-
Finally, displaying the information on the screen
The application, or “app,” downloaded to the phone plays a primary role, but is enabled by:
-
The phone’s operating system and associated services
-
The phone’s hardware
-
The telecommunications infrastructure (cell phone towers, long distance fiber optic cables, switching offices, and much more)
Of course, without the banking systems on the other end, there is no bank balance to transmit. These systems are similar, but on a much larger scale than our friend’s device:
-
Internet and middleware services to receive the request from the international network
-
Application services to validate the user’s identity and route the request to the appropriate handling service
-
Data services to store the user’s banking information (account identity and transactions) along with millions of other customers
-
Many additional services to detect fraud and security attacks, report on utilization, identify any errors in the systems, and much more
-
Physical data centers full of computers and associated hardware including massive power and cooling infrastructure, and protected by security systems and personnel
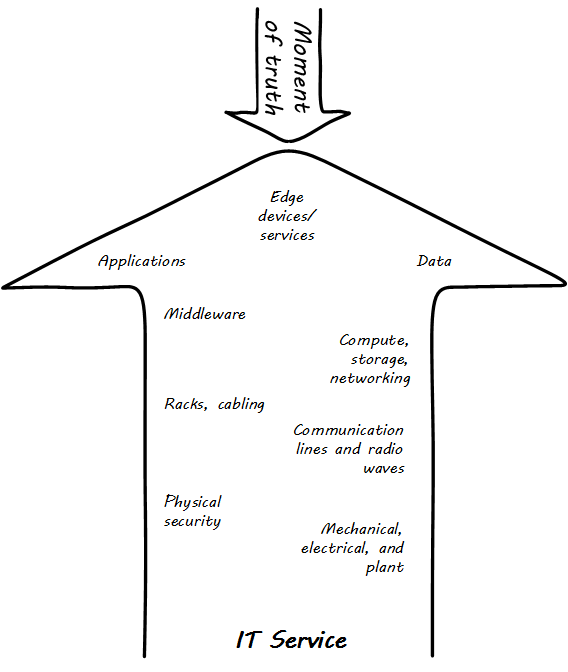
Consider: what does all this mean to our user? Does she care about cell phone towers, or middleware, or triply-redundant industrial-strength Power Distribution Units? Usually, not in the least. Therefore, as we study this world, we need to maintain awareness of her perspective. Our friend is seeking some value that IT uniquely can enable, but does not want to consider all the complexity that goes into it. She just wants to go out with friends. The moment of truth (The IT stack supports the moment of truth) depends on the service; the service may contain great complexity, but part of its success lies in shielding the user from that complexity.
|
Important
|
Always remember the user’s experience. Information technology has a well deserved reputation for being too complicated for end users—for example, trying to do something that should be simple, and finding oneself in a technical conversation about network settings. |
1.4.2. What versus how
This fundamental tension between what a system is supposed to do, versus how it does it, pervades IT management and will likely define your career. “Don’t trouble me with the details, just give me the results” is the overall theme, and we encounter this reaction to complexity in many aspects of life.
Terminology is important. We need to have a more precise way of describing the IT, beyond just saying there is “lots” of it. A variety of terms are used in this text:
-
Digital product
-
IT service
-
Application
-
IT system
-
IT infrastructure
We also see discussion of components, resources, subsystems, assets, and many more terms.
|
Warning
|
There are many debates around these definitions. Sometimes these debates are helpful in clarifying the terminology you want to use on your team. But sometimes the debates don’t add any value. Beware of anyone who claims there is a “best practice” here. |
In general, in this book, we will use the following definitions:
-
A digital or IT service is defined primarily in terms of WHAT not HOW
-
Defining an IT system may include a discussion of both WHAT it does and HOW it does it
-
An “application” usually means some IT service or system for end users who are not primarily concerned with IT other than wanting to get something done with it (e.g., go out to dinner)
-
“Infrastructure” usually means some IT service or system that primarily supports OTHER IT services or systems (e.g.,a network “service” is not usually useful to end users without additional application services)
Finally, the concept of the “IT stack” is important. Notice how the different technology layers appear “stacked” in The IT stack supports the moment of truth. Layered approaches to understanding IT are common, such as the OSI model and the Zachman framework (see Further Reading for useful references).
1.5. The digital service lifecycle
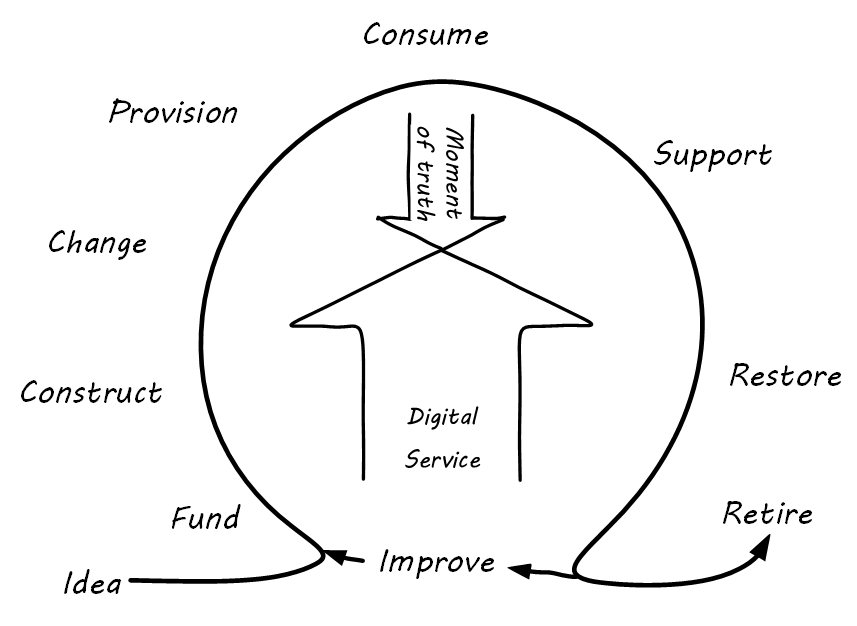
We’ve established that the digital or IT service is based on a complex stack of technology, from local devices to global networks to massive data centers. Software and hardware are layered together in endlessly inventive ways to solve problems people did not even know they had ten years ago. However, these IT service systems must come from somewhere. They must be designed, built, and operated, and continually improved over time. A simple representation of the IT service lifecycle is shown in The essential states of the digital service (or product).
-
It starts with an idea. Someone has an insight into an IT-enabled value proposition that can make a profit, or better fulfill a mission.
-
The idea must garner support and resources so that it can be built.
-
The idea is then constructed, at least as an initial proof of concept or Minimum Viable Product (in the language of Ries' Lean Startup). Construction is assumed to include an element of design; in this textbook, construction and design are not represented as two large-scale separate phases. The activities may be distinct, but are conducted within a context of faster design-build iterations.
-
There is a critical state transition however that will always exist. Initially, it is the change from OFF to ON when the system is first constructed, activated, and made available for access. After the system is ON, there are still distinct changes in state when new features are deployed, or incorrect behaviors (“bugs” or “defects”) are rectified.
-
The system may be ON, but it is not delivering value until the user can access it. Sometimes, that may be as simple as providing someone with a network address, but usually there is some initial “provisioning” of system access to the user, who needs to identify themselves.
-
The system can then deliver services (moments of truth) to the end users. It may deliver millions or billions of such experiences, depending on its scale and how one might choose to count the subjective concept of value experience.
-
The user may have access, but may still not receive value, if they do not understand the system well enough to use it. Whether via a formal service desk, or informal social media channels, users of IT services will require and seek support on how to maximize the value they are receiving from the system.
-
Sometimes, support requests indicate that something is wrong with the system itself. If the system is no longer delivering value experiences (bank balances, restaurant reservations, traffic directions) then some action must be taken promptly to restore service.
-
All of the previous states in the lifecycle generate data and insight that lead to further evolution of the system. There is a wide variety of ways systems may evolve: new user functionality, more stable technology, increased system capacity, and more. Such motivations result in new construction and changes to the existing system, and so the cycle begins again.
-
… Unless … the system’s time is at an end. If there is no reason for the system to exist any longer, it should be retired.
|
Note
|
System retirement is often more complex and expensive than expected, and there are many examples of systems surviving well beyond the point they deliver value. |
So we see that the digital service/product evolves over time, through many repetitions (“iterations”) of the improvement cycle. This entire process, from idea to decommissioning (“inspire to retire”) can be understood as the service lifecycle (The digital service lifecycle).
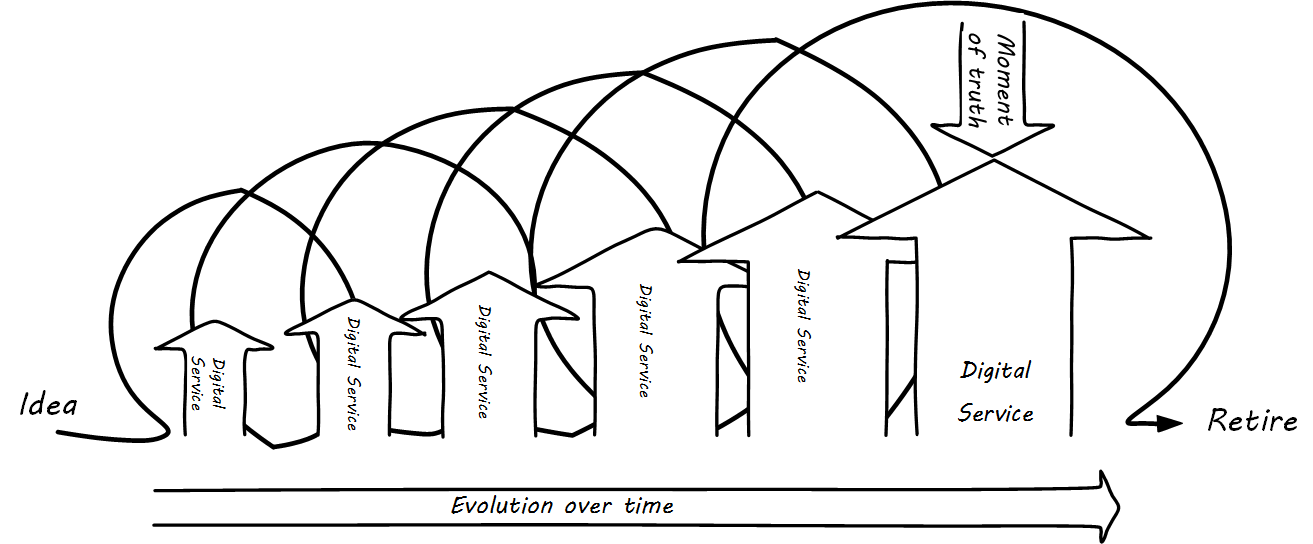
We can combine the service experience (moment of truth) with the service/product lifecycle into the “dual-axis value chain” (originally presented in [25]):
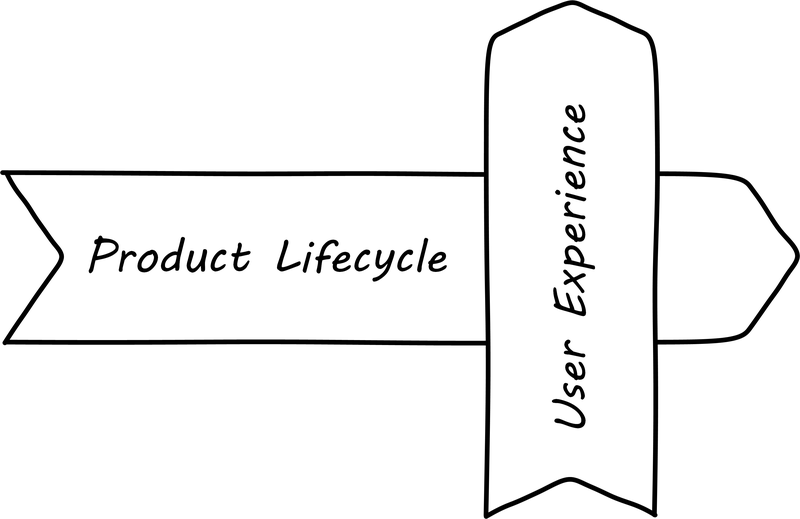
The dual-axis value chain can be seen in many representations of IT and digital delivery systems. Product evolution flows from right to left, while day-to-day value flows up, through the technical stack. It provides a basis for (among other things) thinking about the IT user, customer, and sponsor, which we will cover in the next section.
1.6. Defining consumer, customer, and sponsor
In understanding IT value, it is essential to clarify the definitions of user, customer, and sponsor, and understand their perspectives and motivations. Sometimes, the user is the customer. But more often, the user and the customer are different, and one may additionally need to distinguish the role of system or service sponsor.
The following definitions may help:
-
The consumer (sometimes called the user) is the person actually interacting with the IT or digital service.
-
The customer is a source of revenue for the service. If the service is part of a profit center, the customer is the person actually purchasing the product (e.g.,demand deposit banking). If the service is part of a cost center (e.g.,an HR system), the customer is best seen as an internal executive, as the actual revenue-producing customers are too far removed.
-
The sponsor is the person who authorizes and controls the funding used to construct and operate the service.
Depending on the service type, these roles can be filled by the same or different people. Here are some examples:
| Example | Consumer | Customer | Sponsor | Notes |
|---|---|---|---|---|
Online banking |
Bank account holder |
Vice president, consumer banking |
Customer-facing profit center with critical digital component |
|
Online restaurant reservation application |
Restaurant customers |
Restaurant owners |
Product owner |
Profit-making digital product |
Enterprise human resources application |
HR analyst |
Vice president, HR |
Cost center funded through corporate profits |
|
Online video streaming service |
End video consumer (e.g.,any family member) |
Streaming account holder (e.g.,parent) |
Streaming video product owner |
Profit-making digital product |
Social traffic application |
Driver |
Advertiser, data consumer |
Product owner |
Profit-making digital product |
So, who paid for our user’s enjoyment? The bank and restaurant both had clear motivation for supporting a better online experience, and people now expect that service organizations provide this. The bank experiences less customer turnover and increased likelihood that customers add additional services. The restaurant sees increased traffic and smoother flow from more efficient reservations. Both see increased competitiveness.
The traffic application is a somewhat different story. While it is an engineering marvel, there is still some question as to how to fund it long term. It requires a large user base to operate, and yet end consumers of the service are unlikely to pay for it. At this writing, the service draws on advertising dollars from businesses wishing to advertise to passersby, and also sells its real-time data on traffic patterns to a variety of customers, such as developers considering investments along given routes.
This last example well illustrates the maxim (attributed to media theorist and writer Douglas Rushkoff [255]) that “if you don’t know how the product is making money, you are the product.”
1.7. Understanding digital context
most startups can only guess who their customers are and what markets they are in [31 p. 37].
The Four Steps to the Epiphany
As you consider embarking on a journey of IT or digital value, you need to orient to your surroundings and create an initial proposal or plan for how you will proceed. If you are actually a startup, you need a business plan. If you are working as an intrapreneur in a larger organization, you will still need some kind of formal proposal. This section describes some tools and thinking approaches that may be useful at this very earliest stage. There are more focused, product-specific approaches in the Chapter 4 section on product discovery techniques.
1.7.1. Market-facing, supporting, back office
In the previous section we discussed the question of “who pays/who benefits” for the service, proposing that the service consumer, the service customer, and the service sponsor might be three distinct roles (sometimes collapsing into two or one individuals).
We see this again in how we can categorize the "customers” of IT services and systems. Roughly, such services can be:
-
Directly market- and consumer-facing (e.g., Facebook), to be used by external consumers and paid for by either them or closely associated customers (e.g., Netflix, or an online banking system).
-
Customer “supporting” systems, such as the online system that a bank teller uses when interacting with a customer. Customers do not interact directly with such systems, but customer-facing representatives do, and problems with such systems may be readily apparent to the end customer.
-
Completely “back-office” systems (HR, payroll, marketing, etc.).
Note, however, that (especially in the current digitally transforming market) a service previously thought of as “back-office” (when run internally) becomes “market-facing” when developed as a profit-seeking offering. For example, an HR system built internally is “back-office,” but Workday is a directly market-facing product, even though the two services may be similar in functionality. In other words, it’s all relative. Especially when products are not market-facing, we start to run into the problem of distinguishing discovery versus design, as we discuss below.
1.7.2. Diffusion theory and other approaches
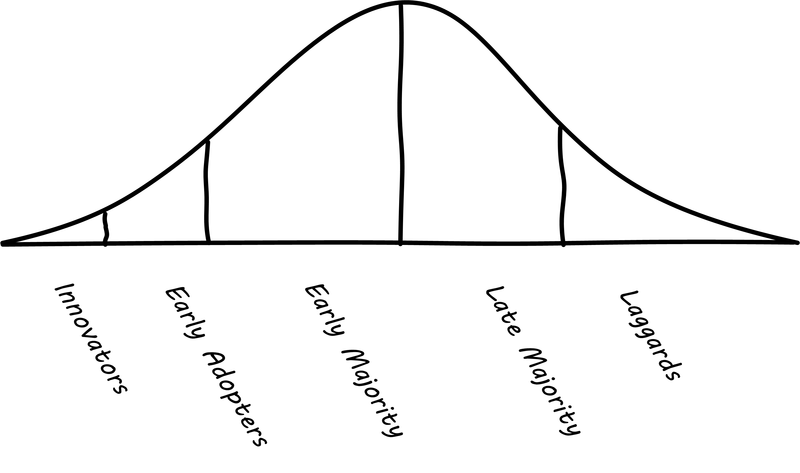
As you start to think about digital value, you must think about the context for your startup or product idea. What is the likelihood of its being adopted? Is it part of a broader “movement” of technological innovation? Where is the customer base in terms of its willingness to adopt the innovation? A well known approach is the idea of "diffusion theory,” first researched by Everett Rogers and proposed in his Diffusion of Innovations [225].
Rogers' research proposed the idea of “Adopter Categorization on the Basis of Innovativeness,” with a well-known graphic (Technology adoption categories[4]).
Rogers went on to characterize the various stages:
-
Innovators: Venturesome risk-takers
-
Early adopters: Opinion leaders
-
Early majority: Deliberative, numerous
-
Late majority: Skeptical, also numerous
-
Laggards: Traditional, isolated, conservative
Rogers' figure was popularized in the following variation by Geoffrey Moore [189] in his bestseller Crossing the Chasm (Purported “chasm” between adopter categories [5]).
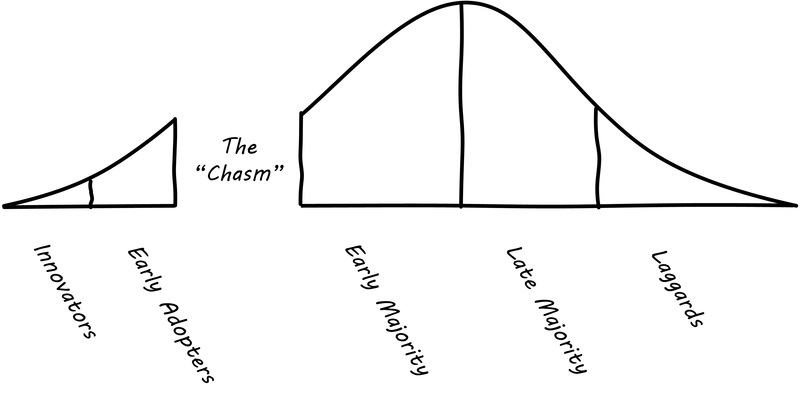
You’ll see Moore’s variation often, but you should be aware that Rogers himself (the person who has researched the data) says that (p. 282):
Past research shows no support for this claim of a “chasm” between certain adopter categories. On the contrary, innovativeness, if measured properly, is a continuous variable and there are no sharp breaks or discontinuities between adjacent adopter categories (although there are important differences between them).
The idea of technology diffusion frames the problem for us, but we need more. Steve Blank, in his influential book The Four Steps to Epiphany [31 p. 31], argues there are four categories for startups:
-
Startups that are entering an existing market
-
Startups that are creating an entirely new market
-
Startups that want to re-segment an existing market as a low-cost entrant
-
Startups that want to re-segment an existing market as a niche player
Understanding which category you are attempting is critical, because “the four types of startups have very different rates of customer adoption and acceptance.”
Another related and well known categorization of competitive strategies comes from Michael Treacy and Fred Wiersma [269]:
-
Customer intimacy
-
Product leadership
-
Operational excellence
It is not difficult to categorize well known brands in this way:
| Customer intimacy | Product leadership | Operational excellence |
|---|---|---|
Nordstrom |
Apple |
Dell Technologies |
Home Depot |
Nike |
Walmart |
However, deciding which strategy to pursue as a startup may require some experimentation.
1.7.3. Business discovery approaches
Startups that survive the first few tough years do not follow the traditional product-centric launch model espoused by product managers or the venture capital community … In particular, the winners invent and live by a process of customer learning and discovery. I call this process “Customer Development,” a sibling to “Product Development,” and each and every startup that succeeds recapitulates it, knowingly or not.
The Four Steps to Epiphany
Let’s start with two well known approaches that can help you bridge from an understanding of your product context, to an effective vision for building and sustaining a product:
-
Alexander Osterwalder’s Business Model Canvas
-
Eric Ries' Lean Startup
Business model canvas
One recent book that’s been influential among enterpreneurs is Alex Osterwalder’s Business Model Generation [205]. This book is perhaps best known for introducing the concept of the Business Model Canvas, which it defines as “A shared language for describing, visualizing, assessing, and changing business models.” The Business Model Canvas uses nine major categories to describe the business model:
-
Key Partners
-
Key Activities
-
Value Proposition
-
Customer Relationships
-
Customer Segments
-
Key Resources
-
Channels
-
Cost Structure
-
Revenue Streams
and suggests they be visualized as in Business Model Canvas [6]
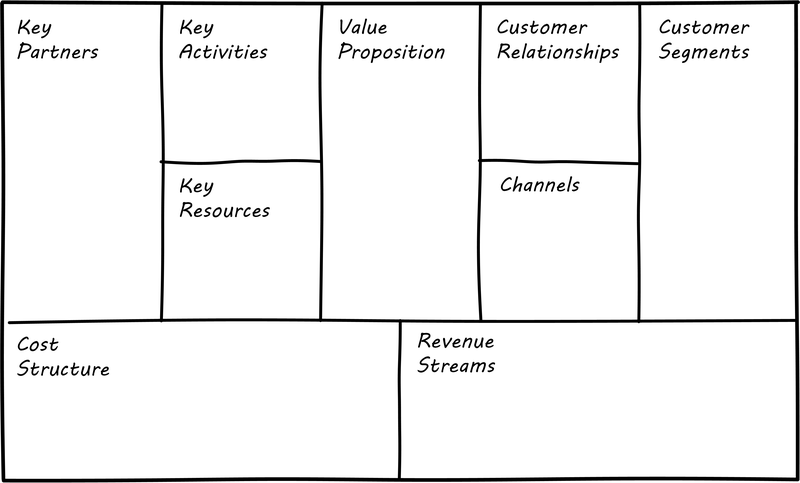
The canvas is then used in collaborative planning, e.g., as a large format wall poster where the business team can brainstorm, discuss, and fill in the boxes (e.g., what is the main “Value Proposition"? Mobile bank account access?).
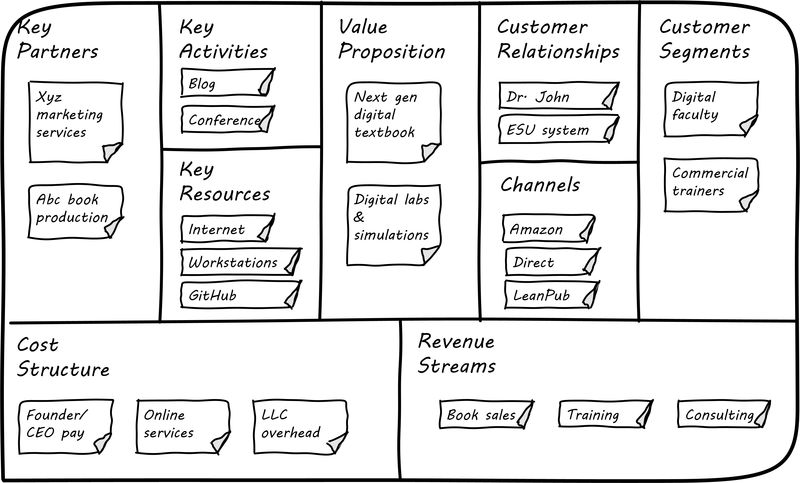
Osterwalder and his colleagues, in Business Model Generation and the follow-up Value Proposition Design [206], suggest a wide variety of imaginative and creative approaches to developing business models and value propositions, in terms of patterns, processes, design approaches, and overall strategy.
Business case analysis
There are a wide variety of analysis techniques for making a business case at a more detailed level. Donald Reifer, in Making the Software Business Case [218], lists:
-
Breakeven analysis
-
Cause-and-effect analysis
-
Cost/benefit analysis
-
Value chain analysis
-
Investment opportunity analysis
-
Pareto analysis
-
Payback analysis
-
Sensitivity analysis
-
Trend analysis
A primary theme of this book is that empirical, experimental approaches are essential to digital management. Any analysis, carried to an extreme without a sound basis in real data, risks becoming a “castle in the air.” But when you are putting real money on the line (even the opportunity costs of the time you are spending on your startup), it is advisable to look at the decision from various perspectives. These techniques can be useful for that purpose. However, once you have some indication there might be business value in a given idea, applying Lean Startup techniques may be more valuable than continuing to analyze.
Lean Startup
The goal of a startup is to figure out the right thing to build — the thing customers want and will pay for — as quickly as possible. In other words, the Lean Startup is a new way of looking at the development of innovative new products that emphasizes fast iteration and customer insight, a huge vision, and great ambition, all at the same time.
The Lean Startup
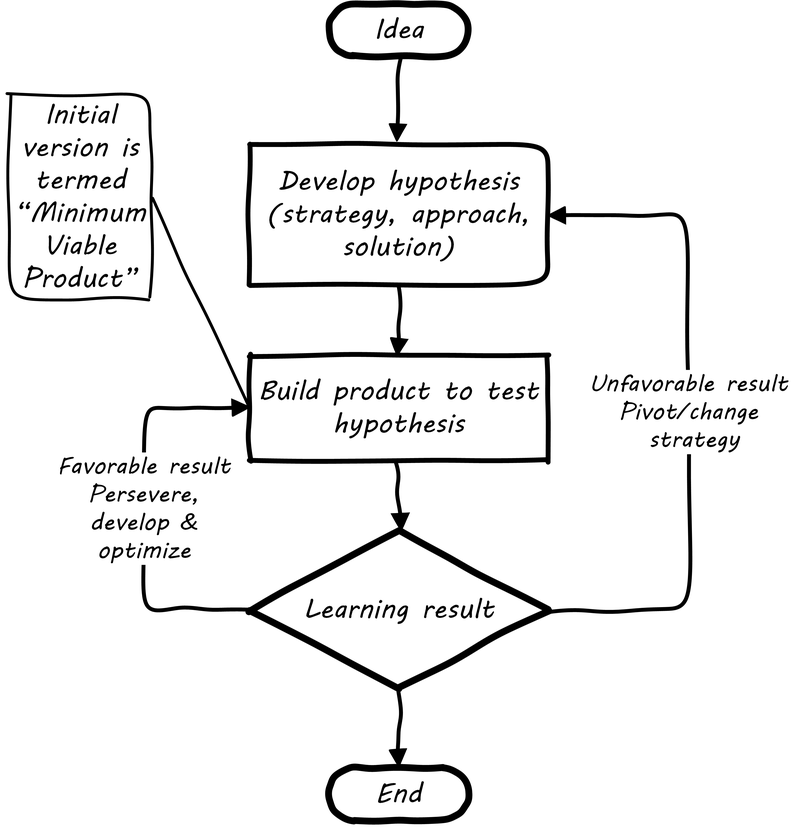
Lean Startup is a philosophy of entrepreneurship developed by Eric Ries [222]. It is not specific to IT; rather, it is broadly applicable to all attempts to understand a product and its market. (According to our definition of product management a workable market position is essential to any product).
The idea of the Lean Startup has had profound influence on product design, including market-facing and even internal IT systems. It is grounded in Agile concepts such as:
“Do the simplest thing that could possibly work.”
Lean Startup calls for an iterative “Build-Measure-Learn” cycle (Lean Startup flowchart [7]). Repeating this cycle frequently is the essential process of building a successful startup (whatever the digital proportion).
-
Develop an idea for a Minimum Viable Product (MVP)
-
Measure its effectiveness in the market (internal/external)
-
Learn from the experiment
-
Decide to persevere or pivot (change direction while leveraging momentum)
-
New idea development, evolution of MVP
Flowcharts such as the one shown are often seen to describe the Lean Startup process. We will go into much more depth on product management in Chapter 4 and Part III.
1.8. Conclusion
In this chapter, we discussed the basic questions of IT value and how it is experienced and developed. Through the mechanism of a hypothetical modern IT user, we covered (at a very high level) the necessary ingredients of the IT experience. We considered the user’s moment of truth, and the massive IT complexity that sustains it. We also discussed a high-level lifecycle model for IT applications and services, and explored some initial definitions for user, customer, and sponsor — critical distinctions to make in an age of digital transformation.
As you proceed into the course, the key takeway from this chapter is “why IT?” Why do people need it, and how is it valuable? That should always remain at the top of your mind as you proceed in your IT education.
1.8.1. Discussion questions
-
Discuss: How does IT contribute to your enjoyment of life and experiences of value?
-
Read "Apps Are Wrecking Mom-and-Pop Pizza Shops" and discuss whether “IT matters” to the local pizzerias.
-
Read the Wikipedia articles on mainframe computing and Amazon Web Services and discuss with your team. What has changed in computing? What remains the same?
1.8.2. Research & practice
-
Go to any popular online service (Facebook, Netflix, Flickr, etc.).. How would you describe the “moments of truth” or value experiences these sites offer users? There may be several.
-
On your own or with a team, develop an idea for an IT-based product you could take to market. Present to the class.
-
(Continued) Who are the user, customer, and sponsor of your product?
-
Research and apply one of the business case analysis techniques to your idea.
1.8.3. Further reading
Books
-
Code, Charles Petzold
-
The Information, James Glieck
-
The Lean Startup, Ries
Articles